Details more than 157 threats posed to information security best
Details images of threats posed to information security by website nanoginkgobiloba.vn compilation. Checking-up on Health: Ransomware Accounts for 54% of Cybersecurity Threats — ENISA. What is Threat Detection & Response I Resources I Anomali. Principles of Information Security, Fourth Edition ppt download
 Top Cyber Security Risks & Their Precautions – #1
Top Cyber Security Risks & Their Precautions – #1
 The Top 5 Cybersecurity Threats | Pitman Training – #2
The Top 5 Cybersecurity Threats | Pitman Training – #2

 NSC Information Technology Group – Cyber Security Awareness. | Facebook – #4
NSC Information Technology Group – Cyber Security Awareness. | Facebook – #4
 Cyber security trends 2023 | Allianz Commercial – #5
Cyber security trends 2023 | Allianz Commercial – #5
 Principles of Information Security, 2nd Edition1 Threats and Attacks. – ppt download – #6
Principles of Information Security, 2nd Edition1 Threats and Attacks. – ppt download – #6
 The energy sector threat: How to address cybersecurity vulnerabilities | McKinsey – #7
The energy sector threat: How to address cybersecurity vulnerabilities | McKinsey – #7
 What is Cybersecurity? (A Quick Guide)- Sprinto – #8
What is Cybersecurity? (A Quick Guide)- Sprinto – #8
 Public Safety Cybersecurity | CISA – #10
Public Safety Cybersecurity | CISA – #10
 Top 10 Types of Network Security Threats: List and Defenses – #11
Top 10 Types of Network Security Threats: List and Defenses – #11
 Cyber threats to Canada’s democratic process : July 2021 update – Canadian Centre for Cyber Security – #12
Cyber threats to Canada’s democratic process : July 2021 update – Canadian Centre for Cyber Security – #12
 5 Website Security Threats and Solutions | Indusface Blog – #13
5 Website Security Threats and Solutions | Indusface Blog – #13
 Question 4 Imagine that you are an information security con.pdf – #14
Question 4 Imagine that you are an information security con.pdf – #14
 What is Cybersecurity? Know Cybersecurity Skills, Career Path, Eligibility & Courses | Shiksha Online – #15
What is Cybersecurity? Know Cybersecurity Skills, Career Path, Eligibility & Courses | Shiksha Online – #15
 Fact sheet: Cyber security basics for third-party management | AgriFutures Australia – #16
Fact sheet: Cyber security basics for third-party management | AgriFutures Australia – #16
 The 10 Biggest Cyber Security Trends In 2024 Everyone Must Be Ready For Now – #17
The 10 Biggest Cyber Security Trends In 2024 Everyone Must Be Ready For Now – #17
 Common Physical Security Threats and Vulnerabilities (With Examples) – #18
Common Physical Security Threats and Vulnerabilities (With Examples) – #18
![Is a Cyber Security Degree Worth It? [Pros, Cons & Alternatives] Is a Cyber Security Degree Worth It? [Pros, Cons & Alternatives]](https://i1.rgstatic.net/publication/320960482_Information_Security_Management_Practices_Case_Studies_from_India/links/5b877e50299bf1d5a7312683/largepreview.png) Is a Cyber Security Degree Worth It? [Pros, Cons & Alternatives] – #19
Is a Cyber Security Degree Worth It? [Pros, Cons & Alternatives] – #19
 The 3 limitations of AI-driven cyber attacks – #20
The 3 limitations of AI-driven cyber attacks – #20
 How do you determine IT security risk? | Netsurion – #21
How do you determine IT security risk? | Netsurion – #21
 The Realistic Journey of Indian Cyber Policy – Defence News | The Financial Express – #22
The Realistic Journey of Indian Cyber Policy – Defence News | The Financial Express – #22
 Emerging Threats And Trends In Protecting Financial Assets – FasterCapital – #23
Emerging Threats And Trends In Protecting Financial Assets – FasterCapital – #23
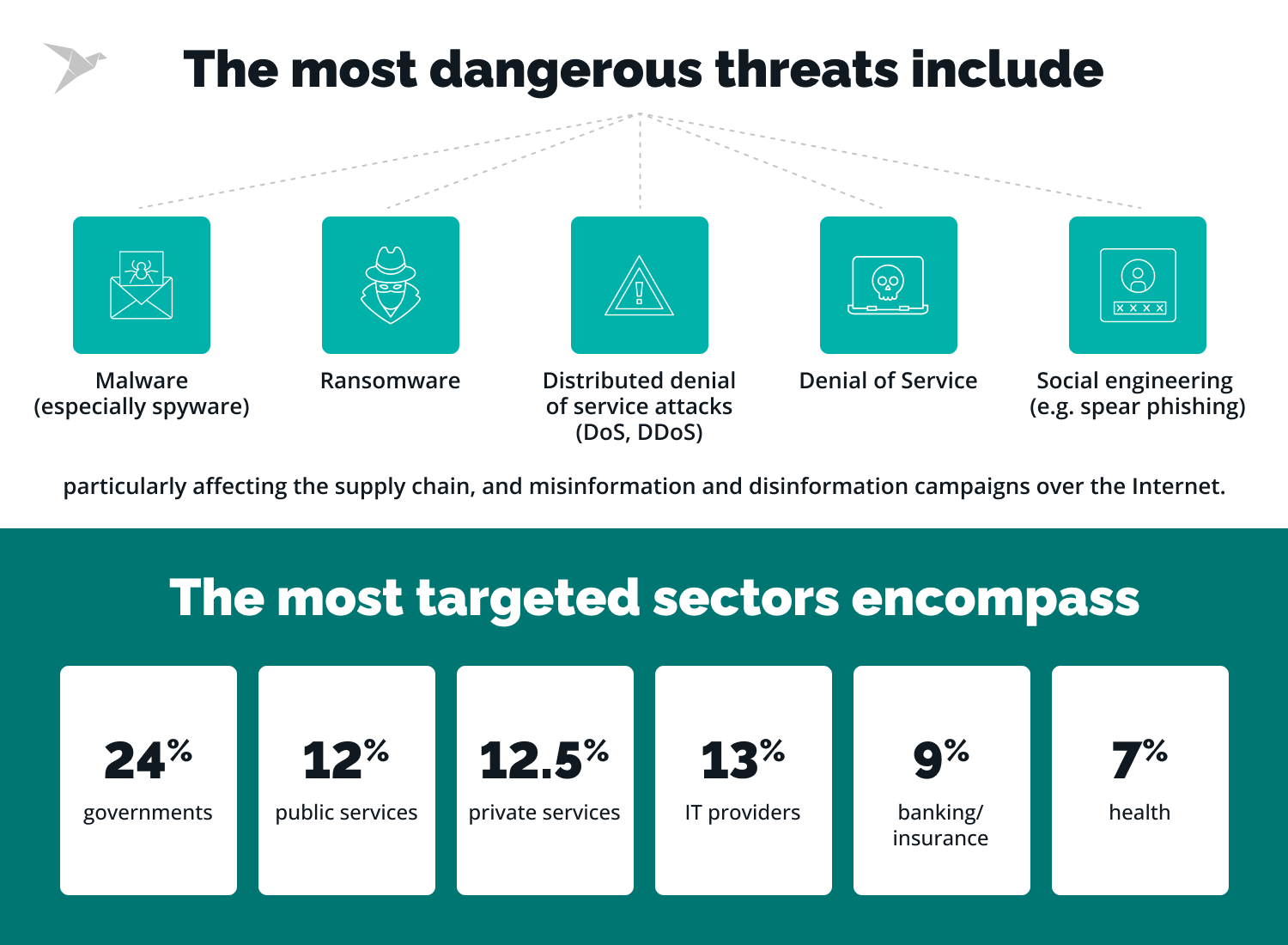
 10 Information Security Threats in 2018 | LimeProxies – #24
10 Information Security Threats in 2018 | LimeProxies – #24
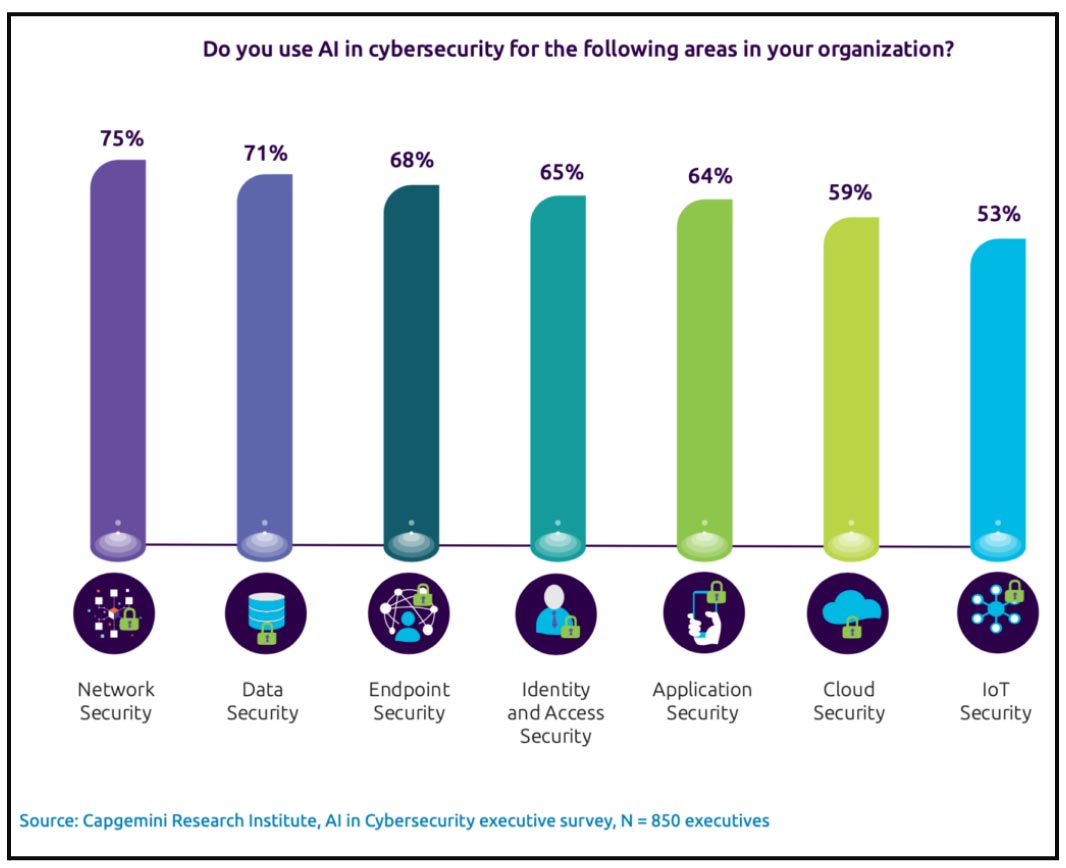
 Hong Kong Cyber Security Incidents on the Rise HKCERT Urges the Community to Raise Information Security Awareness – #25
Hong Kong Cyber Security Incidents on the Rise HKCERT Urges the Community to Raise Information Security Awareness – #25
 12 Cyber Security Tips for Students at Home & in School – #26
12 Cyber Security Tips for Students at Home & in School – #26
 Frontiers | Cyber Security Threats and Challenges in Collaborative Mixed-Reality – #27
Frontiers | Cyber Security Threats and Challenges in Collaborative Mixed-Reality – #27
 SOLUTION: Principles of information security chapter 2 – Studypool – #28
SOLUTION: Principles of information security chapter 2 – Studypool – #28
 How to Design and Configure Secure Industrial Networks – #29
How to Design and Configure Secure Industrial Networks – #29
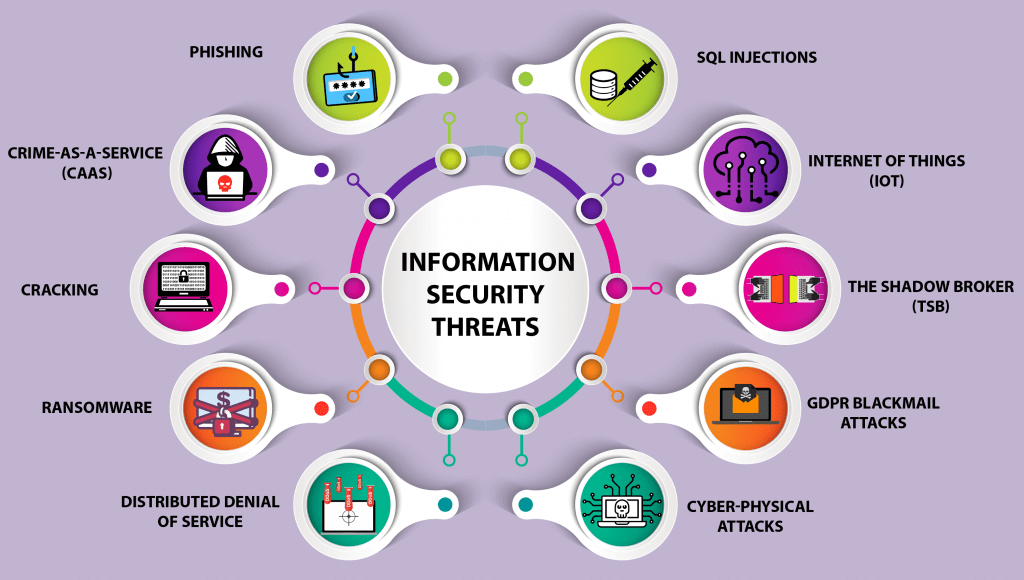
 The Significance of Cyber Security in Software Development – #30
The Significance of Cyber Security in Software Development – #30
 Microsoft report shows increasing sophistication of cyber threats – Microsoft On the Issues – #31
Microsoft report shows increasing sophistication of cyber threats – Microsoft On the Issues – #31
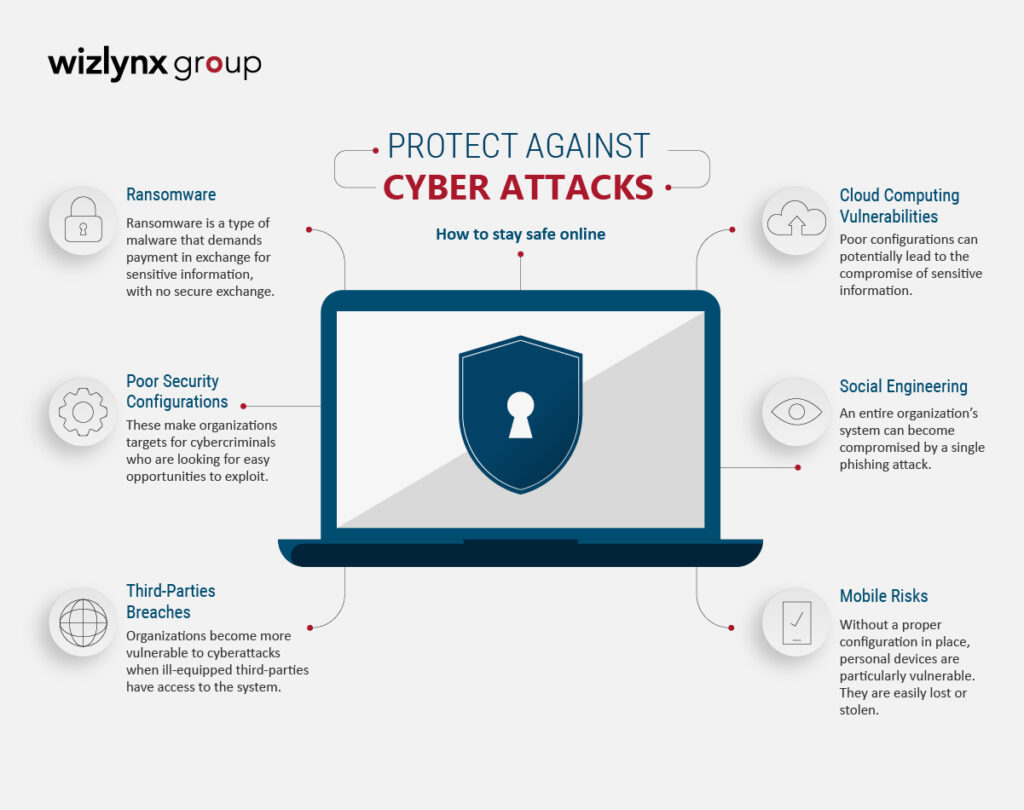 How does the Information Environment Threaten National Security? (video blog) | U.S. GAO – #32
How does the Information Environment Threaten National Security? (video blog) | U.S. GAO – #32
 CVE-2023-50387 and CVE-2023-50868 — DNS Exploit KeyTrap Posed Major Internet Threat | Akamai – #33
CVE-2023-50387 and CVE-2023-50868 — DNS Exploit KeyTrap Posed Major Internet Threat | Akamai – #33
- physical security threats
- computer security threats and solutions
- top 10 cyber security threats
 Microsoft Digital Defense Report 2023 (MDDR) | Microsoft Security Insider – #34
Microsoft Digital Defense Report 2023 (MDDR) | Microsoft Security Insider – #34
 12 Types of Security Threat and How to Protect Against Them – #35
12 Types of Security Threat and How to Protect Against Them – #35
 Risks Posed by Cyberattacks to Health Care Companies – #36
Risks Posed by Cyberattacks to Health Care Companies – #36
 10 Cyber Security Threats In 2017 | Purple Griffon – #37
10 Cyber Security Threats In 2017 | Purple Griffon – #37
 Decoding 2024’s Threat Landscape – QuoIntelligence – #38
Decoding 2024’s Threat Landscape – QuoIntelligence – #38
- types of cyber security jobs
- types of security risks
- types of security threats
 The Threats of Cyber Security – 348 Words | Essay Example – #39
The Threats of Cyber Security – 348 Words | Essay Example – #39
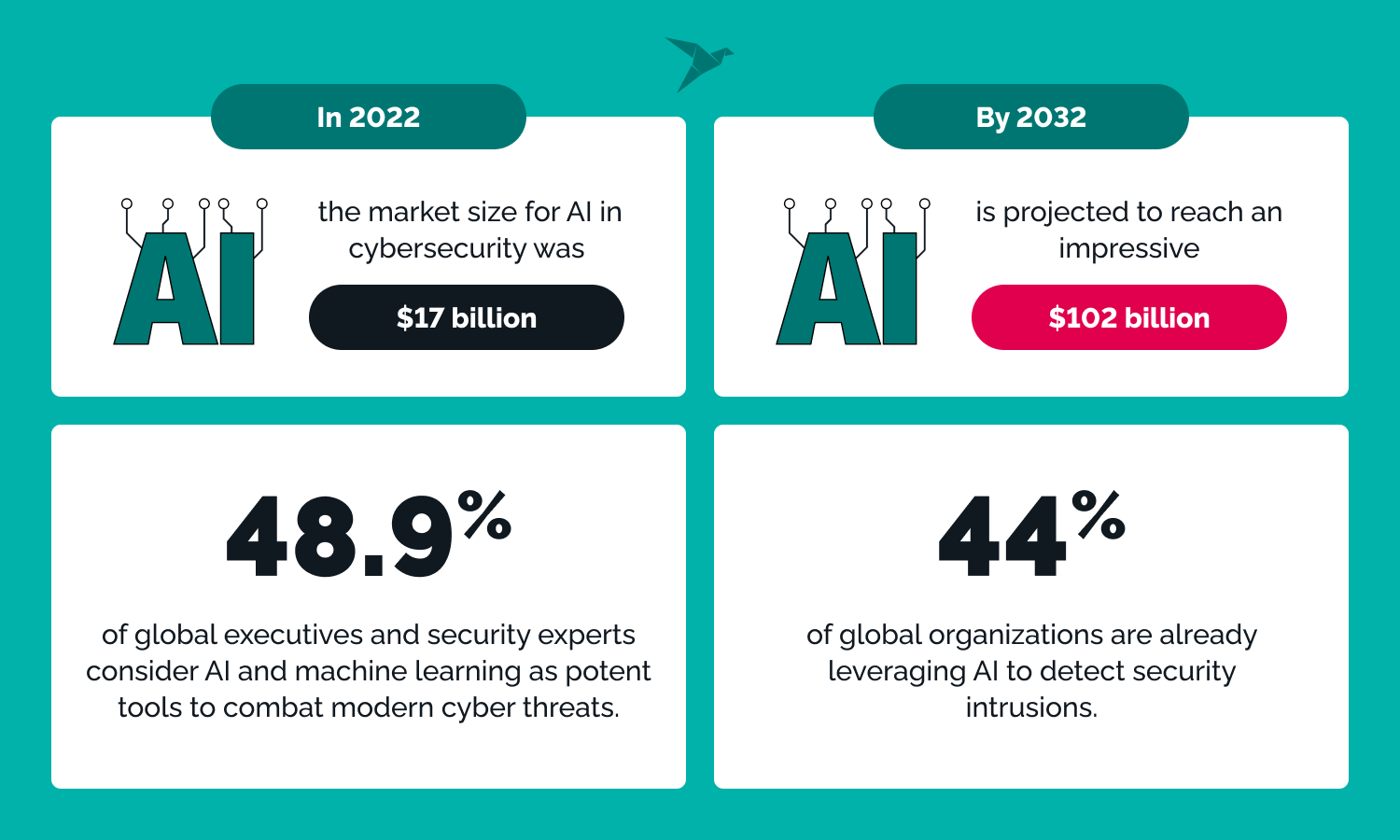 Introduction to Internal Security of India – #40
Introduction to Internal Security of India – #40
 Prevent ransomware attacks with email security – #41
Prevent ransomware attacks with email security – #41
- background cyber security threats
- cyber security threats images
- types of threats
 An Introduction to Cybersecurity Awareness – SSL Dragon – #42
An Introduction to Cybersecurity Awareness – SSL Dragon – #42
 Cybersecurity in Schools: The Importance of Cyber Security in the Education Sector – #43
Cybersecurity in Schools: The Importance of Cyber Security in the Education Sector – #43
 Mitigating Insider Threats: Safeguarding Client Information within Law Firms – Cyber Security Solutions, Compliance, and Consulting Services – IT Security – #44
Mitigating Insider Threats: Safeguarding Client Information within Law Firms – Cyber Security Solutions, Compliance, and Consulting Services – IT Security – #44
 7 Easy Methods To Protect Yourself From Cybersecurity Threats – #45
7 Easy Methods To Protect Yourself From Cybersecurity Threats – #45
 What is Cyber Security? Definition, Types and Importance – Blockchain Council – #46
What is Cyber Security? Definition, Types and Importance – Blockchain Council – #46
 AI & its Implications on Information Security | itnext.in – #47
AI & its Implications on Information Security | itnext.in – #47
 The seven themes driving the future of cybersecurity – Help Net Security – #48
The seven themes driving the future of cybersecurity – Help Net Security – #48
 Cybersecurity – On the Issues – #49
Cybersecurity – On the Issues – #49
 Emerging Technologies And Their Impact On Cyber Security – #50
Emerging Technologies And Their Impact On Cyber Security – #50
 The Pros and Cons of Cybersecurity: What You Need to Know – #51
The Pros and Cons of Cybersecurity: What You Need to Know – #51
 Security | Alcatel-Lucent Enterprise – #52
Security | Alcatel-Lucent Enterprise – #52
- types of cyber security images
- cyber security threats
- internal threats
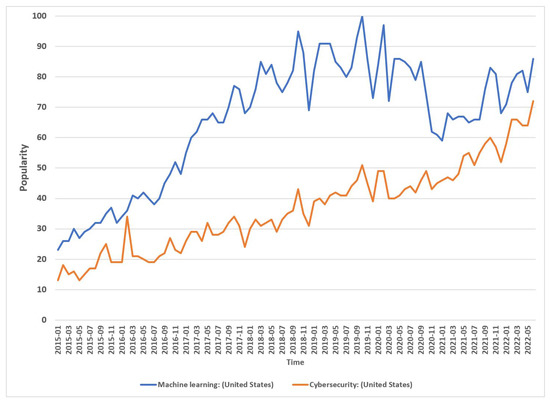 Checking-up on Health: Ransomware Accounts for 54% of Cybersecurity Threats — ENISA – #53
Checking-up on Health: Ransomware Accounts for 54% of Cybersecurity Threats — ENISA – #53
 GovInfoSecurity.com – #54
GovInfoSecurity.com – #54
 Cybersecurity in Banking Sector: Importance, Threats, Challenges – #55
Cybersecurity in Banking Sector: Importance, Threats, Challenges – #55
 Top 7 Artificial intelligence Data Security Threats to AI and ML – #56
Top 7 Artificial intelligence Data Security Threats to AI and ML – #56
 Mobile security: What it is and why you need it – Norton – #57
Mobile security: What it is and why you need it – Norton – #57
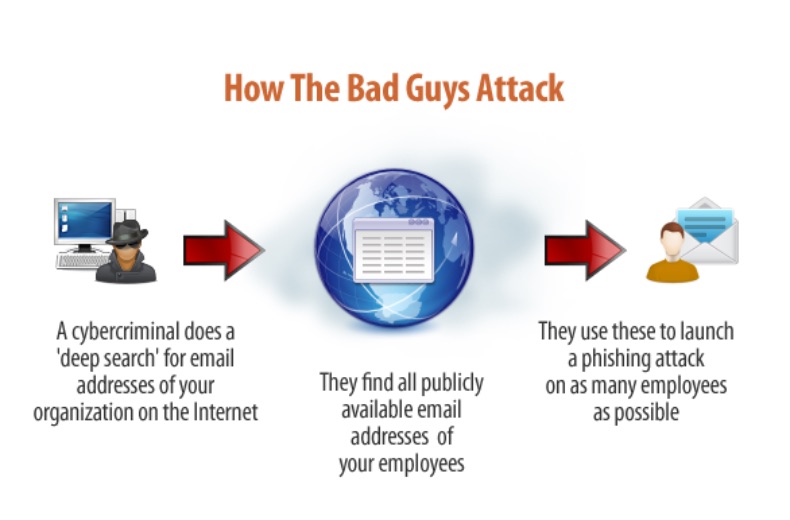
 Module 3-cyber security | PDF – #58
Module 3-cyber security | PDF – #58
 Mastering Modern Cybersecurity Threats: Your Essential Guide | Prey Blog – #59
Mastering Modern Cybersecurity Threats: Your Essential Guide | Prey Blog – #59
 Cyber Security Industry Outlook Size, Industry Share| Trends – #60
Cyber Security Industry Outlook Size, Industry Share| Trends – #60
 Friend or Foe? Exploring the Relationship Between AI and Cybersecurity | by Tutort Academy | Feb, 2024 | Medium – #61
Friend or Foe? Exploring the Relationship Between AI and Cybersecurity | by Tutort Academy | Feb, 2024 | Medium – #61
 The Biggest Cyber Security Risks In 2022 – #62
The Biggest Cyber Security Risks In 2022 – #62
 What Is Unauthorized Access? 5 Key Prevention Best Practices – #63
What Is Unauthorized Access? 5 Key Prevention Best Practices – #63
 Response to General Assembly resolution 68/243 – #64
Response to General Assembly resolution 68/243 – #64
 An Introduction to Cyber Threat Intelligence: Key Concepts and Principles | Tripwire – #65
An Introduction to Cyber Threat Intelligence: Key Concepts and Principles | Tripwire – #65
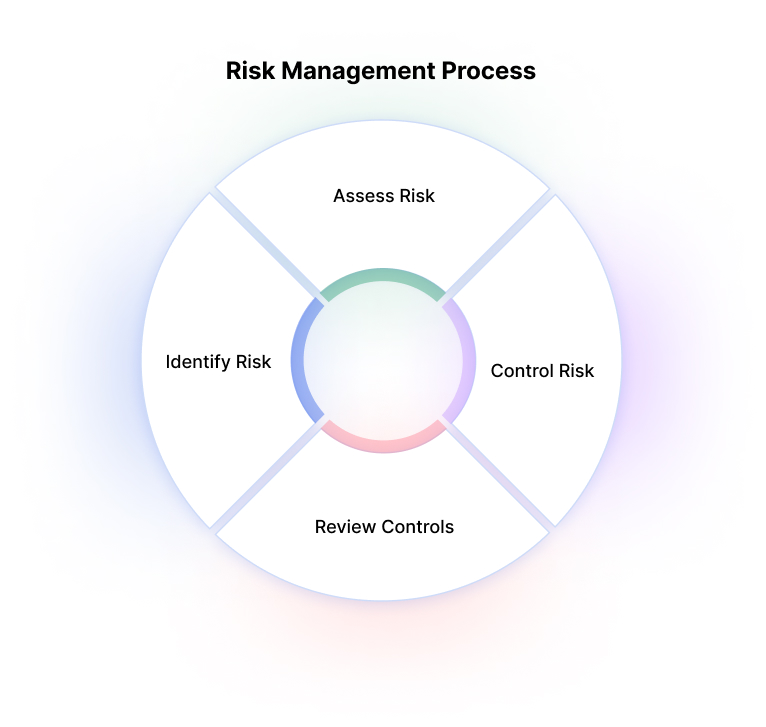
 Learning Objectives Upon completion of this material, you should be able to: – ppt download – #66
Learning Objectives Upon completion of this material, you should be able to: – ppt download – #66
 Management of Cyber Security Supply Chain Risks | Australian National Audit Office (ANAO) – #67
Management of Cyber Security Supply Chain Risks | Australian National Audit Office (ANAO) – #67
 What is Threat Intelligence and Why is it Important? | – #68
What is Threat Intelligence and Why is it Important? | – #68
 What is IT Security? | IBM – #69
What is IT Security? | IBM – #69
 The Top 10 Cybersecurity Threats to Digital Banking and How to Guard Against Them – GuardRails – #70
The Top 10 Cybersecurity Threats to Digital Banking and How to Guard Against Them – GuardRails – #70
 2024 Cybersecurity Predictions | LogRhythm – #71
2024 Cybersecurity Predictions | LogRhythm – #71
 Top 9 Cybersecurity Threats and Vulnerabilities – Compuquip – #72
Top 9 Cybersecurity Threats and Vulnerabilities – Compuquip – #72
 Analyse the multidimensıonal challenges posed by external state and non-state actors, to the internal security of India. Also discuss measures required to be taken to combat these threats. (250 Words 15 Marks) – – #73
Analyse the multidimensıonal challenges posed by external state and non-state actors, to the internal security of India. Also discuss measures required to be taken to combat these threats. (250 Words 15 Marks) – – #73
 The Future of Cybersecurity Lies in Blockchain Technology – #74
The Future of Cybersecurity Lies in Blockchain Technology – #74
 Let’s Get Physical: Cyber Security in an Era of Global Instability – #75
Let’s Get Physical: Cyber Security in an Era of Global Instability – #75
 AI-powered chatbots: the threats to national security are only beginning | CSO Online – #76
AI-powered chatbots: the threats to national security are only beginning | CSO Online – #76
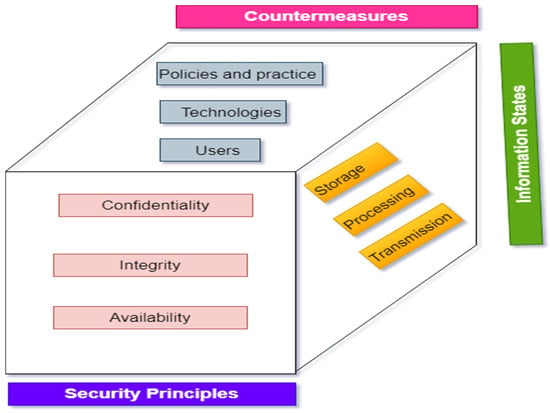 Nation-State Cyber Actors | Cybersecurity and Infrastructure Security Agency CISA – #77
Nation-State Cyber Actors | Cybersecurity and Infrastructure Security Agency CISA – #77
 A History of Information Security From Past to Present – #78
A History of Information Security From Past to Present – #78
 Frontiers | Cyber security threats: A never-ending challenge for e-commerce – #79
Frontiers | Cyber security threats: A never-ending challenge for e-commerce – #79
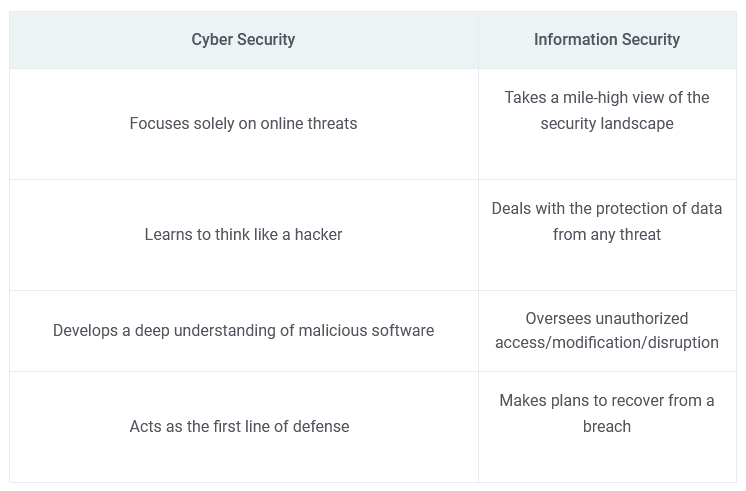 Top 8 Cybersecurity Trends for 2024 | Blog | Code Intelligence – #80
Top 8 Cybersecurity Trends for 2024 | Blog | Code Intelligence – #80
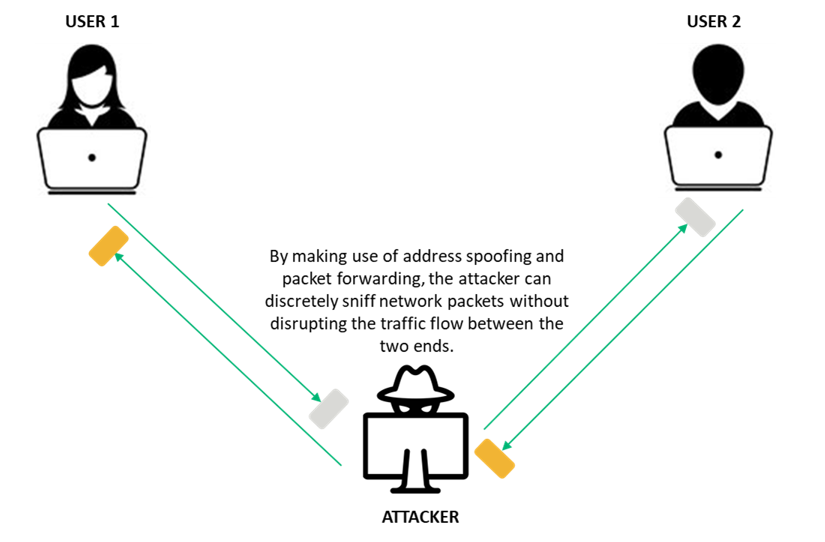
 Network Attacks and Network Security Threats – #81
Network Attacks and Network Security Threats – #81
 Who is the Prime Target for Cyber Attacks? – #82
Who is the Prime Target for Cyber Attacks? – #82
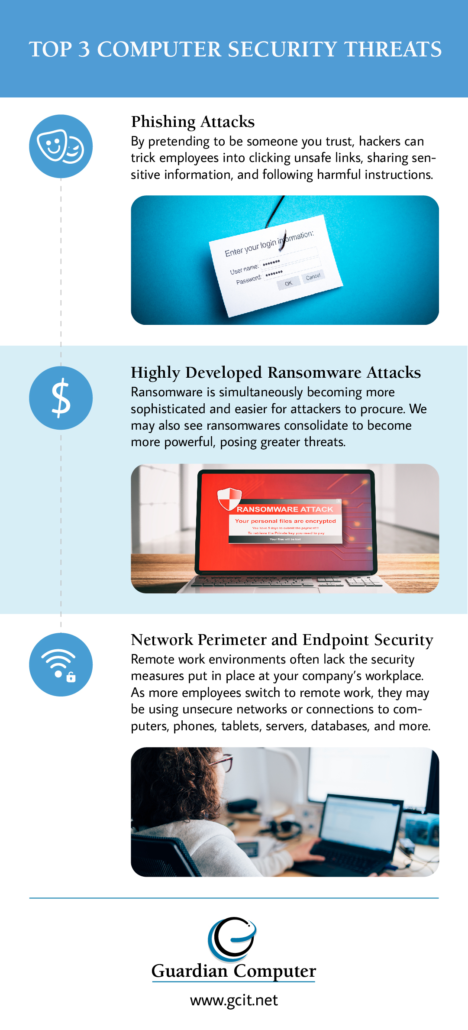 Top cybersecurity trends of 2023 | Security Magazine – #83
Top cybersecurity trends of 2023 | Security Magazine – #83
 Top 10 Computer Security Threats to Business IT in 2021 – Guardian Computer – #84
Top 10 Computer Security Threats to Business IT in 2021 – Guardian Computer – #84
 Top 10 Challenges of Cyber Security Faced in 2022 | UNext – #85
Top 10 Challenges of Cyber Security Faced in 2022 | UNext – #85
 Cyber Task Forces: Building Alliances to Improve the Nation’s Cybersecurity — FBI – #86
Cyber Task Forces: Building Alliances to Improve the Nation’s Cybersecurity — FBI – #86
 10 Cyber Security Problems Nearly Every Organization Struggles With | Rasmussen University – #87
10 Cyber Security Problems Nearly Every Organization Struggles With | Rasmussen University – #87
- internet security threats
- top cyber security threats
- internet threats
 The new risks ChatGPT poses to cyber security – #88
The new risks ChatGPT poses to cyber security – #88
 Identity-based security threats are growing rapidly: report | CSO Online – #89
Identity-based security threats are growing rapidly: report | CSO Online – #89
- diagram cyber security threats
- cybersecurity challenges
 Making Your Business Ready for Cyber Security Challenges – #90
Making Your Business Ready for Cyber Security Challenges – #90
 Enterprise risk management (ERM): Putting cybersecurity threats into a business context | CSO Online – #91
Enterprise risk management (ERM): Putting cybersecurity threats into a business context | CSO Online – #91
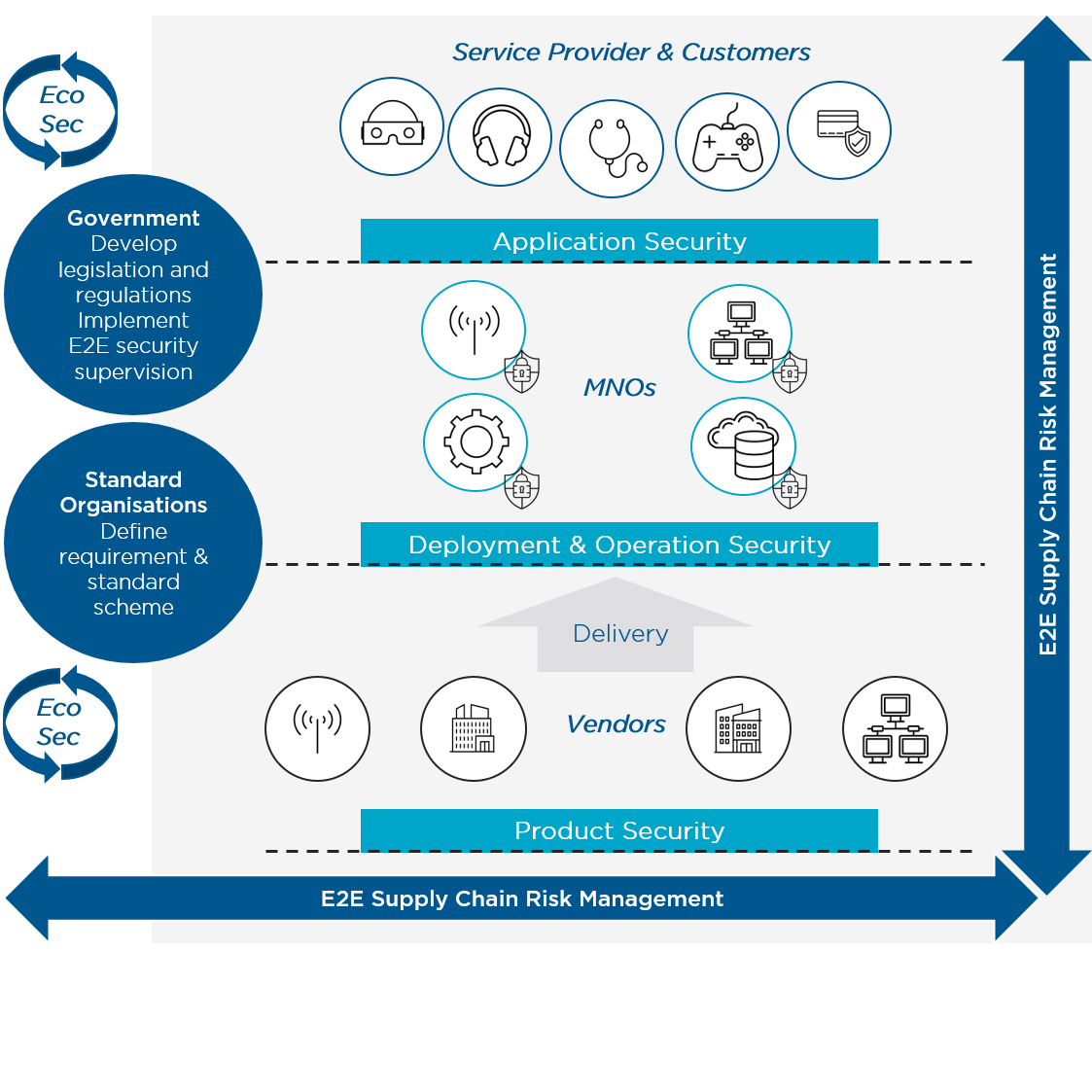
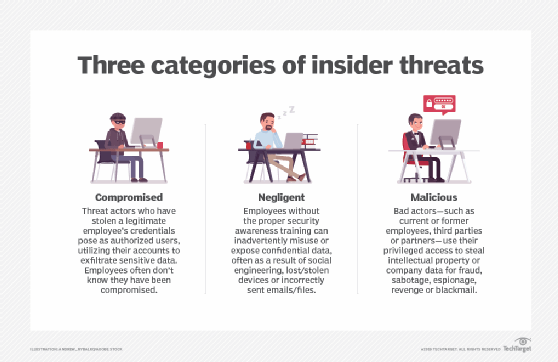 GSMA | GSMA Mobile Cybersecurity Knowledge Base – Security – #92
GSMA | GSMA Mobile Cybersecurity Knowledge Base – Security – #92
- insider threat
- infographic cyber security threats
- cyber threats
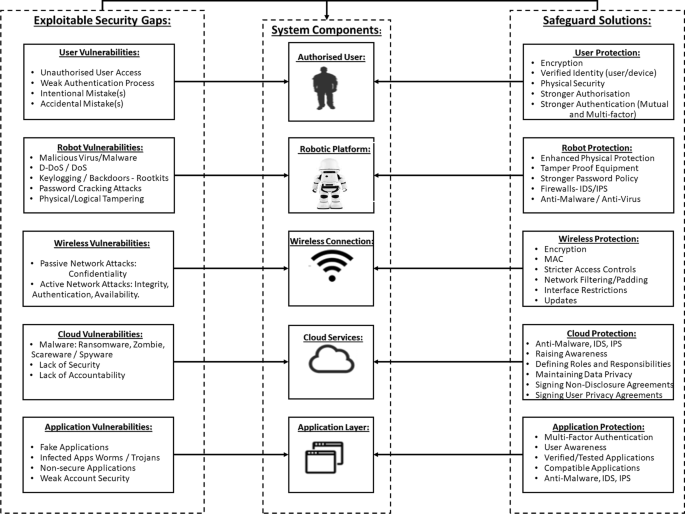
 Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | International Journal of Information Security – #93
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | International Journal of Information Security – #93
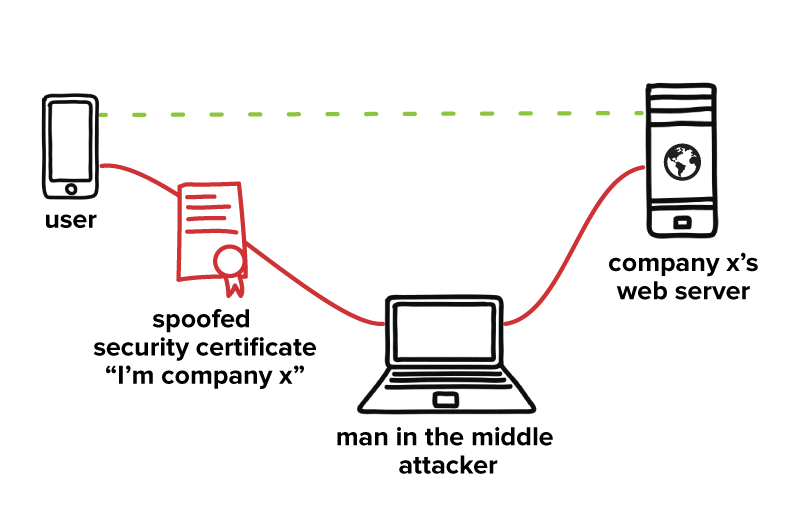 A moment of reckoning: the need for a strong and global cybersecurity response – Microsoft On the Issues – #94
A moment of reckoning: the need for a strong and global cybersecurity response – Microsoft On the Issues – #94
 Threats posed by using RATs in ICS | Securelist – #95
Threats posed by using RATs in ICS | Securelist – #95
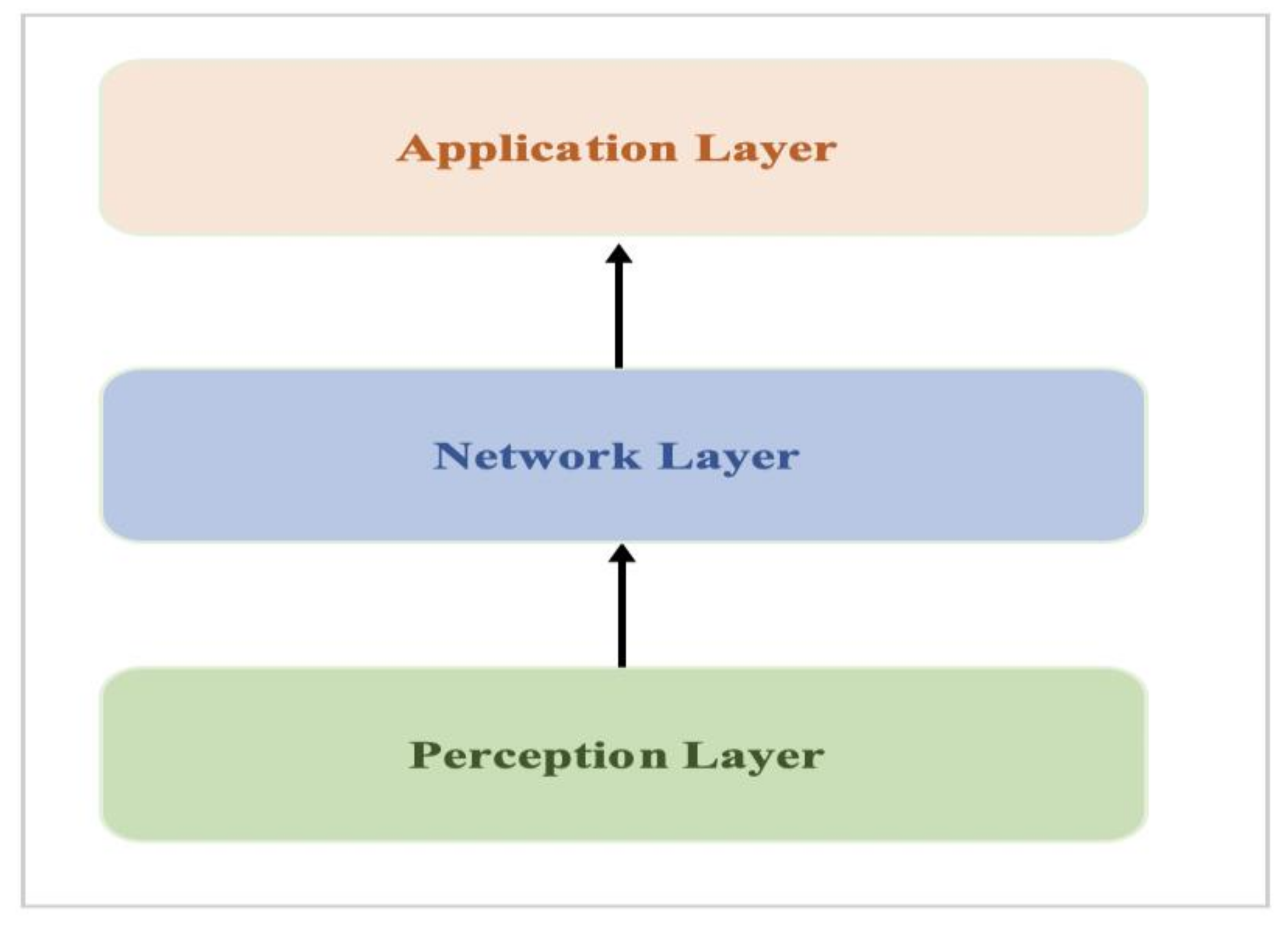
 Sensors | Free Full-Text | Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap – #96
Sensors | Free Full-Text | Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap – #96
- cyber security
- top 10 cyber security threats 2023
- cybersecurity trends
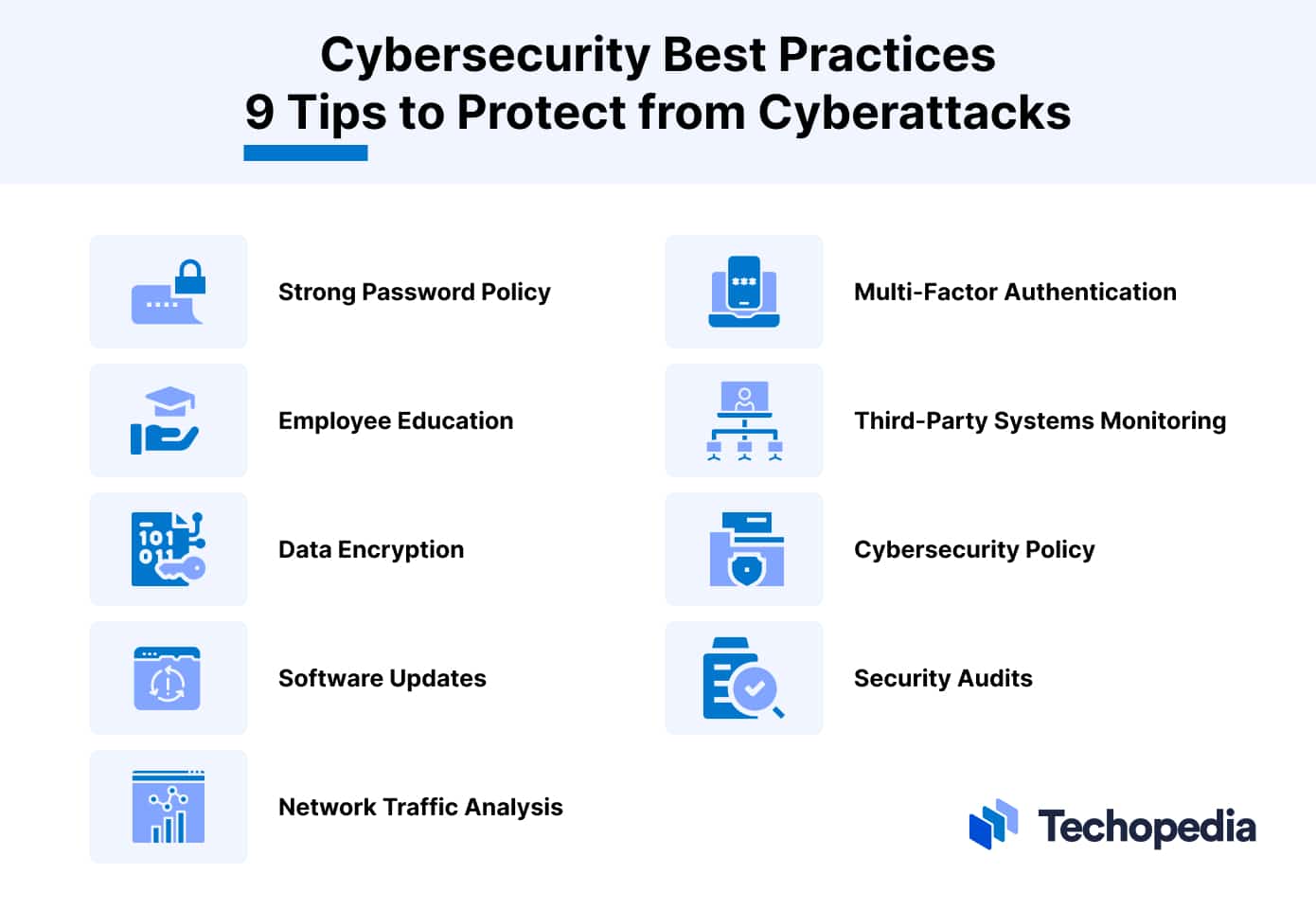 Cyber Security: Identifying threats and risks in the marine industry – #97
Cyber Security: Identifying threats and risks in the marine industry – #97
 PDF) Information Security Management Practices: Case Studies from India – #98
PDF) Information Security Management Practices: Case Studies from India – #98
 DigiTech Conclave 2.0: Covid-19 pandemic has changed the entire architecture of cyber security, ET Government – #99
DigiTech Conclave 2.0: Covid-19 pandemic has changed the entire architecture of cyber security, ET Government – #99
 The Global Security Threat Posed by Southeast Asia’s Criminal Enclaves | United States Institute of Peace – #100
The Global Security Threat Posed by Southeast Asia’s Criminal Enclaves | United States Institute of Peace – #100
 Digital payment: 5 mobile payment security threats | Build38 – #101
Digital payment: 5 mobile payment security threats | Build38 – #101
 Rising Cyber Threats in the Middle East – A Virtual Battleground – SecurityHQ – #102
Rising Cyber Threats in the Middle East – A Virtual Battleground – SecurityHQ – #102
 Understanding Cyber Security Threats: Social Engineering, Malicious Code, and Methods for Detection and Prevention | PDF | Malware | Antivirus Software – #103
Understanding Cyber Security Threats: Social Engineering, Malicious Code, and Methods for Detection and Prevention | PDF | Malware | Antivirus Software – #103
 Cybersecurity Threats | Types & Sources | Imperva – #104
Cybersecurity Threats | Types & Sources | Imperva – #104
 Insider vs. Outsider Data Security Threats – SalvageData – #105
Insider vs. Outsider Data Security Threats – SalvageData – #105
 How to Perform a Cyber Security Risk Assessment – #106
How to Perform a Cyber Security Risk Assessment – #106
 What is a Computer Security Risk? – Definition & Types – Lesson | Study.com – #107
What is a Computer Security Risk? – Definition & Types – Lesson | Study.com – #107
 Increasing Insider Cyber Threats Pose Risks to Aviation – Avionics International – #108
Increasing Insider Cyber Threats Pose Risks to Aviation – Avionics International – #108
 10 cyber security risks in software development and how to mitigate them – DEVTALENTS – #109
10 cyber security risks in software development and how to mitigate them – DEVTALENTS – #109
 A Guide to Using Biometric Software to Stay Ahead of the Security Threats Posed by Quantum Computing – #110
A Guide to Using Biometric Software to Stay Ahead of the Security Threats Posed by Quantum Computing – #110
 10 Common IT Security Risks in the Workplace – #111
10 Common IT Security Risks in the Workplace – #111
 The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog – #112
The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog – #112
 Cybersecurity Needs Continuous Threat Exposure Management – #113
Cybersecurity Needs Continuous Threat Exposure Management – #113
 Journalists & Cyber Threats – Center for News, Technology & Innovation – #114
Journalists & Cyber Threats – Center for News, Technology & Innovation – #114
- cyber risk
- top 5 cyber security threats
- threats to information security 3 categories
 MSc Cyber Security | Coventry University – #115
MSc Cyber Security | Coventry University – #115
 AI-Driven Threat Hunting: Enhancing Cyber Security through Intelligent Detection – #116
AI-Driven Threat Hunting: Enhancing Cyber Security through Intelligent Detection – #116
 Information Security: Principles, Threats, and Solutions – #117
Information Security: Principles, Threats, and Solutions – #117
 Top 10 Cyber Security Threats | Cyber Magazine – #118
Top 10 Cyber Security Threats | Cyber Magazine – #118
 Protect, Detect and Correct Methodology to Mitigate Incidents – #119
Protect, Detect and Correct Methodology to Mitigate Incidents – #119
 Network security threats and vulnerabilities | NordLayer Learn – #120
Network security threats and vulnerabilities | NordLayer Learn – #120
 Defend Your Digital World: Top 5 Cyber Attacks of 2024 Revealed – #121
Defend Your Digital World: Top 5 Cyber Attacks of 2024 Revealed – #121
 Redefining the Human Factor in Cybersecurity | Kaspersky official blog – #122
Redefining the Human Factor in Cybersecurity | Kaspersky official blog – #122
 Insider threats: What they are and how to prevent them – #123
Insider threats: What they are and how to prevent them – #123
 What Is Cyber Security Risk Mitigation? | RiskXchange – #124
What Is Cyber Security Risk Mitigation? | RiskXchange – #124
 Chapter 2 Cybersecurity Risk Management, Risk Assessment and Asset Evaluation | Protection of Transportation Infrastructure from Cyber Attacks: A Primer | The National Academies Press – #125
Chapter 2 Cybersecurity Risk Management, Risk Assessment and Asset Evaluation | Protection of Transportation Infrastructure from Cyber Attacks: A Primer | The National Academies Press – #125
 Artificial intelligence and cybersecurity in healthcare (YEL2023) – IHF – #126
Artificial intelligence and cybersecurity in healthcare (YEL2023) – IHF – #126
 Cybersecurity Risk Management | Frameworks, Analysis & Assessment | Imperva – #127
Cybersecurity Risk Management | Frameworks, Analysis & Assessment | Imperva – #127
- 7 types of cyber security threats
- information security
- infographic types of cyber attacks
 Defining Insider Threats | CISA – #128
Defining Insider Threats | CISA – #128
 7 Types of Cyber Threat Actors And Their Damage – #129
7 Types of Cyber Threat Actors And Their Damage – #129
 Indie AI Tools: The Unchecked Frontier in Enterprise Security Threats | by Cyber-Oracle | Medium – #130
Indie AI Tools: The Unchecked Frontier in Enterprise Security Threats | by Cyber-Oracle | Medium – #130
 The 9 Most Common Security Threats to Mobile Devices in 2021 – #131
The 9 Most Common Security Threats to Mobile Devices in 2021 – #131
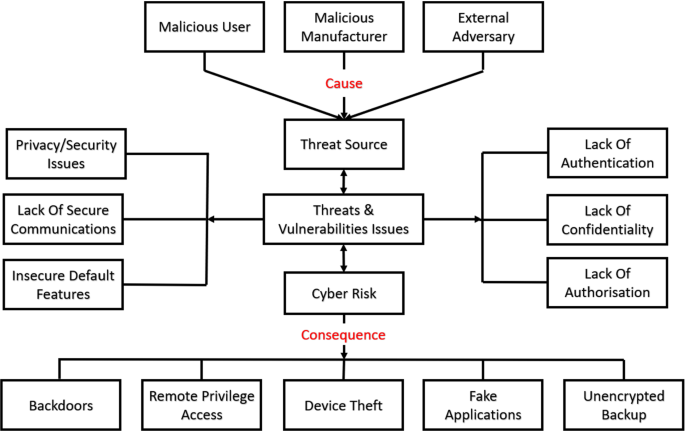 The Effects of Mobile Devices on Cybersecurity Essay Example | Topics and Well Written Essays – 1500 words – #132
The Effects of Mobile Devices on Cybersecurity Essay Example | Topics and Well Written Essays – 1500 words – #132
 PDF) Cyber-Security and Threat Politics: US Efforts to Secure the Information Age – #133
PDF) Cyber-Security and Threat Politics: US Efforts to Secure the Information Age – #133
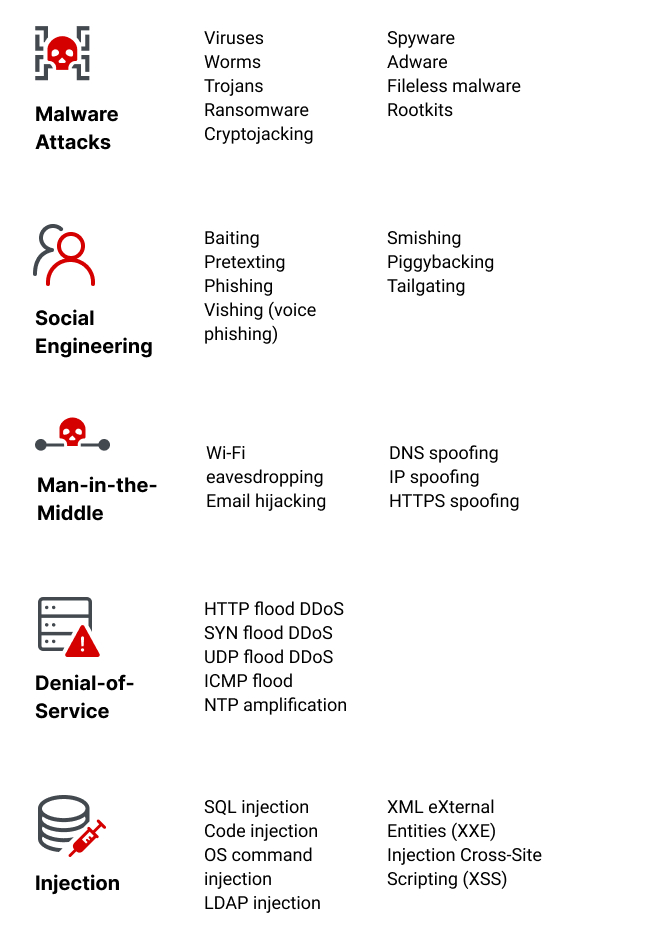 Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions – #134
Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions – #134
 IoT Security Threats and Solutions – #135
IoT Security Threats and Solutions – #135
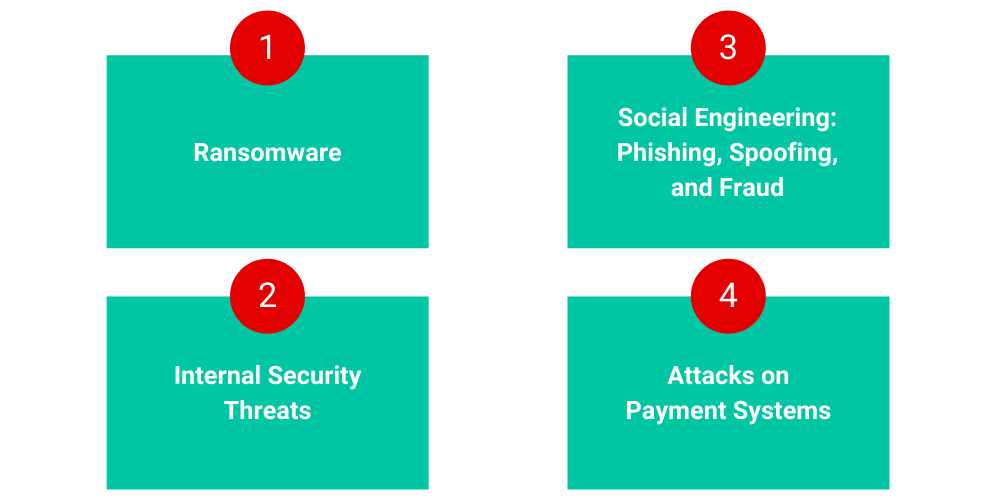 Cybersecurity Vulnerabilities: Types, Examples, and Beyond – Sprinto – #136
Cybersecurity Vulnerabilities: Types, Examples, and Beyond – Sprinto – #136
 Top 10 Uses of AI for Cybersecurity (+14 Applications) | Engati – #137
Top 10 Uses of AI for Cybersecurity (+14 Applications) | Engati – #137
 Cybersecurity strategies in research – Safeguarding Science – #138
Cybersecurity strategies in research – Safeguarding Science – #138
 The New Battlefront: Cyber Security Across the GCC – Gulf International Forum – #139
The New Battlefront: Cyber Security Across the GCC – Gulf International Forum – #139
 Insider Threats in Cybersecurity | Splunk – #140
Insider Threats in Cybersecurity | Splunk – #140
/cybersecurity-trends.webp?width\u003d1200\u0026height\u003d627\u0026name\u003dcybersecurity-trends.webp) Risk, Threat and Vulnerability – How do they Differ? – Bangalore – #141
Risk, Threat and Vulnerability – How do they Differ? – Bangalore – #141
 Solved 1.1.1 It is lunchtime, and Thabo is hungry. He | Chegg.com – #142
Solved 1.1.1 It is lunchtime, and Thabo is hungry. He | Chegg.com – #142
- types of cyber security tools
- cyber threats images
- types of security risks.
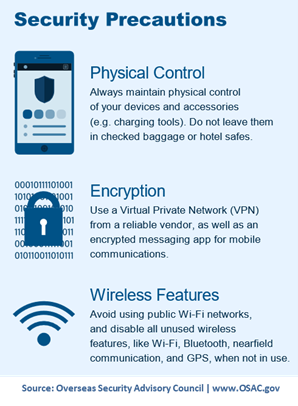 Update your security strategy based on key information learned about threat actors, advises Netskope – Exclusive Networks – Africa – #143
Update your security strategy based on key information learned about threat actors, advises Netskope – Exclusive Networks – Africa – #143
 Proactive Defense: Understanding Threat Detection & Response – #144
Proactive Defense: Understanding Threat Detection & Response – #144
 Vulnerability in Cyber Security – The Guide for Beginners – #145
Vulnerability in Cyber Security – The Guide for Beginners – #145
 What Is Cyber Reconnaissance? – SentinelOne – #146
What Is Cyber Reconnaissance? – SentinelOne – #146
 AI in Cyber Security: Top 6 Use Cases – TechMagic – #147
AI in Cyber Security: Top 6 Use Cases – TechMagic – #147
NSA, U.S. Federal Agencies Advise on Deepfake Threats > National Security Agency/Central Security Service > Press Release View – #148
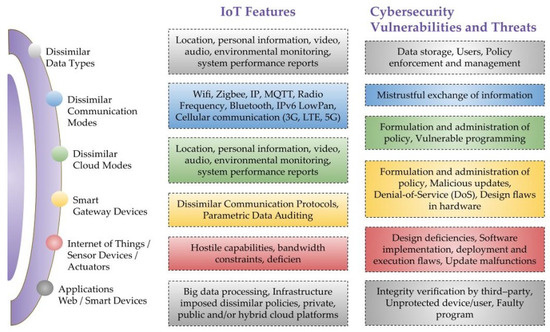 Eight Trends that Pose Data Theft Risks for Organizations | itnext.in – #149
Eight Trends that Pose Data Theft Risks for Organizations | itnext.in – #149
 Cyber Security Breaches Survey 2022 – GOV.UK – #150
Cyber Security Breaches Survey 2022 – GOV.UK – #150
 What is information security compliance? | Blog | OneTrust – #151
What is information security compliance? | Blog | OneTrust – #151
 Top 10 Cybersecurity Threats to Be Wary of in 2024 – #152
Top 10 Cybersecurity Threats to Be Wary of in 2024 – #152
 Artificial Intelligence (AI) in Cyber Security | FDM Group | UK – #153
Artificial Intelligence (AI) in Cyber Security | FDM Group | UK – #153
 What Is Digital Security? Tools and Applications – Panda Security Mediacenter – #154
What Is Digital Security? Tools and Applications – Panda Security Mediacenter – #154
 Threats, Costs and People: Cybersecurity by the Numbers – #155
Threats, Costs and People: Cybersecurity by the Numbers – #155
 Cybersecurity issues in telecoms sector call for protection of network infrastructure and availability – Industrial Cyber – #156
Cybersecurity issues in telecoms sector call for protection of network infrastructure and availability – Industrial Cyber – #156
 PHILIPPINES THREAT OVERVIEW – CYFIRMA – #157
PHILIPPINES THREAT OVERVIEW – CYFIRMA – #157
Posts: threats posed to information security
Categories: Poses
Author: nanoginkgobiloba.vn
