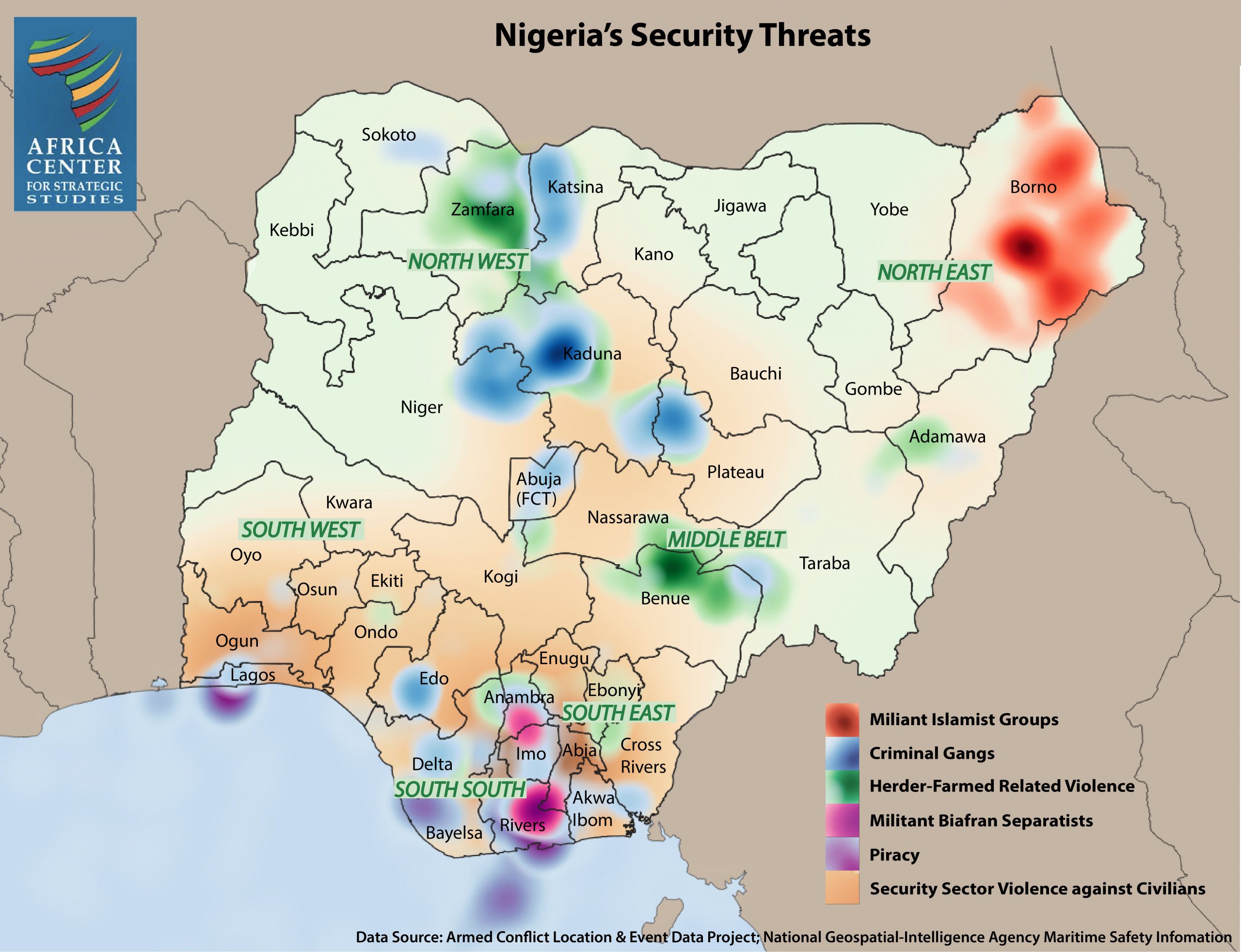
Details 158+ threat posed meaning
Details images of threat posed meaning by website nanoginkgobiloba.vn compilation. miro.medium.com/v2/resize:fit:1146/1*B4Azul5D-guVZ…. PDF) What really is meant by a ‘Substantial Threat’ of Pollution? -an examination of the term’s meaning in the United States and elsewhere | Erika Lindholm – Academia.edu. www.wordstream.com/wp-content/uploads/2022/01/swot…. National Volcano Early Warning System – monitoring volcanoes according to their threat | U.S. Geological Survey. Threat – Definition, Meaning & Synonyms | Vocabulary.com
 Jay Willis on X: “Yes I agree, now is the time for law professors to downplay the threat to free elections posed by an anti-democratic Supreme Court because this process involves legal – #1
Jay Willis on X: “Yes I agree, now is the time for law professors to downplay the threat to free elections posed by an anti-democratic Supreme Court because this process involves legal – #1
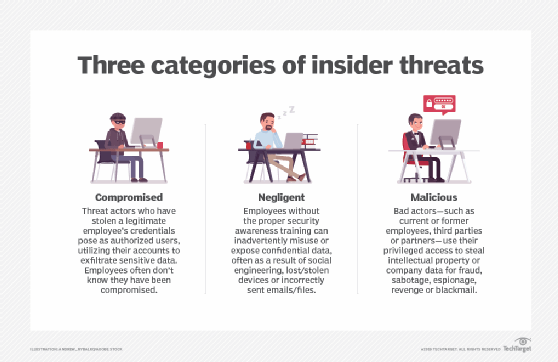
 What Is an Insider Threat? Definition, Types and How to Detect Them – #2
What Is an Insider Threat? Definition, Types and How to Detect Them – #2

 cdn.statcdn.com/Infographic/images/teaser/31605.jp… – #4
cdn.statcdn.com/Infographic/images/teaser/31605.jp… – #4
 CropLife International on X: “The world’s banana supply is under threat from a fungus called TR4, causing the disease banana wilt. Effective pest control products are being researched, but genetic modification techniques – #5
CropLife International on X: “The world’s banana supply is under threat from a fungus called TR4, causing the disease banana wilt. Effective pest control products are being researched, but genetic modification techniques – #5
 study.com/cimages/videopreview/videopreview-full/t… – #6
study.com/cimages/videopreview/videopreview-full/t… – #6
 upload.wikimedia.org/wikipedia/commons/thumb/0/0b/… – #7
upload.wikimedia.org/wikipedia/commons/thumb/0/0b/… – #7
- what is cyber threat
- types of threat actors
- insider threat
 upload.wikimedia.org/wikipedia/commons/6/6f/Spiram… – #8
upload.wikimedia.org/wikipedia/commons/6/6f/Spiram… – #8
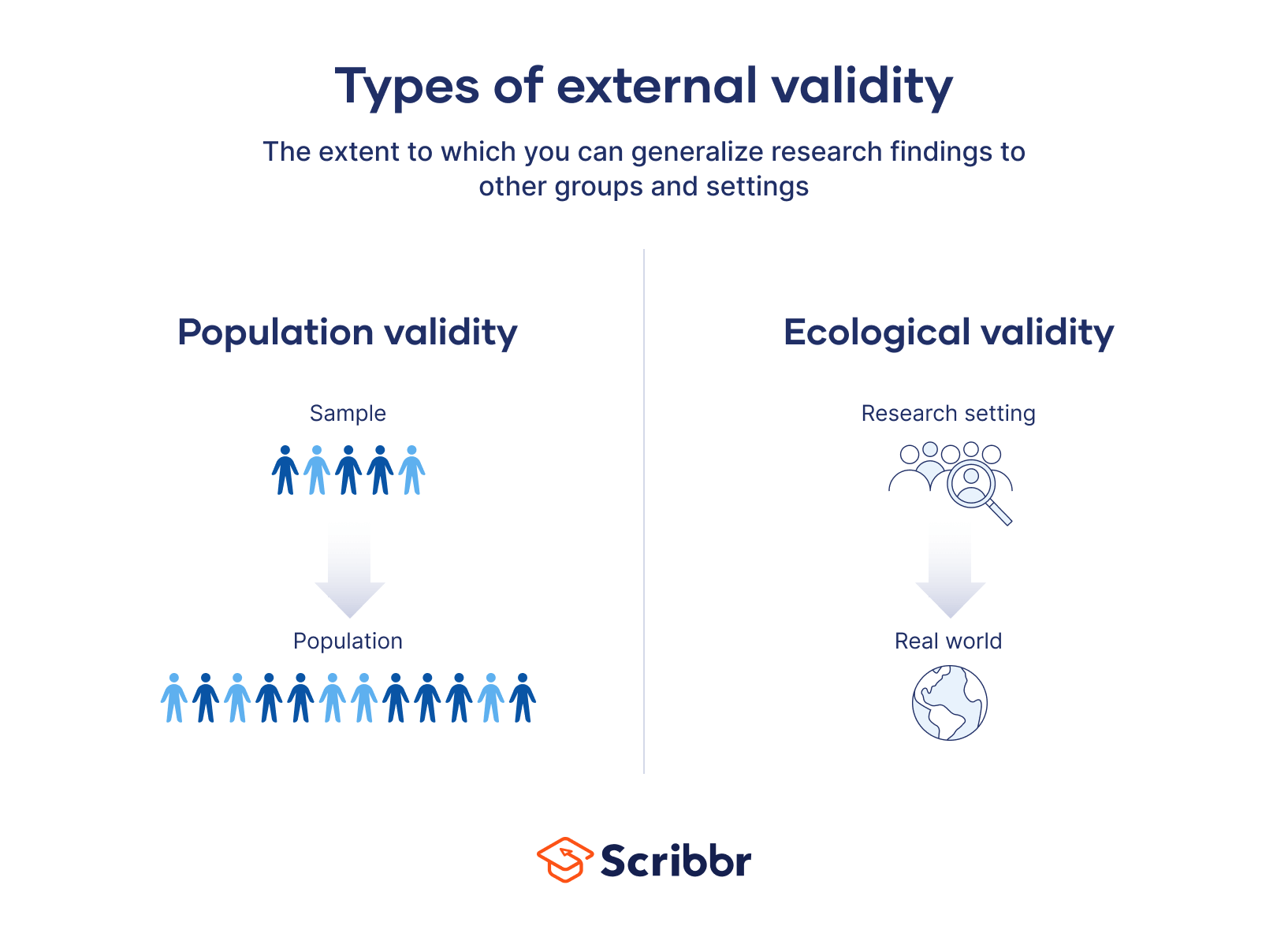
 assets-global.website-files.com/5efc3ccdb72aaa7480… – #10
assets-global.website-files.com/5efc3ccdb72aaa7480… – #10
 www.verywellmind.com/thmb/Ss_799ZuM09ZJH7dCUXuIDGa… – #11
www.verywellmind.com/thmb/Ss_799ZuM09ZJH7dCUXuIDGa… – #11
 owasp.org/www-community/assets/images/UseAndMisuse… – #12
owasp.org/www-community/assets/images/UseAndMisuse… – #12
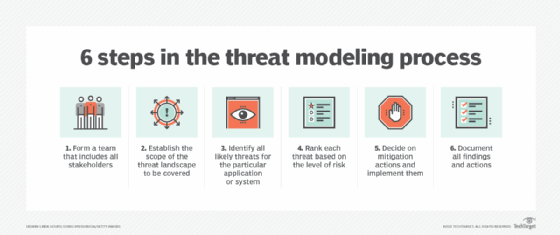
 cdn.ttgtmedia.com/rms/onlineimages/security-6_step… – #13
cdn.ttgtmedia.com/rms/onlineimages/security-6_step… – #13
 cdn.statcdn.com/Infographic/images/normal/31605.jp… – #14
cdn.statcdn.com/Infographic/images/normal/31605.jp… – #14
 What is the meaning of “pose a threat “? – Question about English (US) | HiNative – #15
What is the meaning of “pose a threat “? – Question about English (US) | HiNative – #15
 Difference Between Risk, Threat, and Vulnerability – Intellipaat – #16
Difference Between Risk, Threat, and Vulnerability – Intellipaat – #16
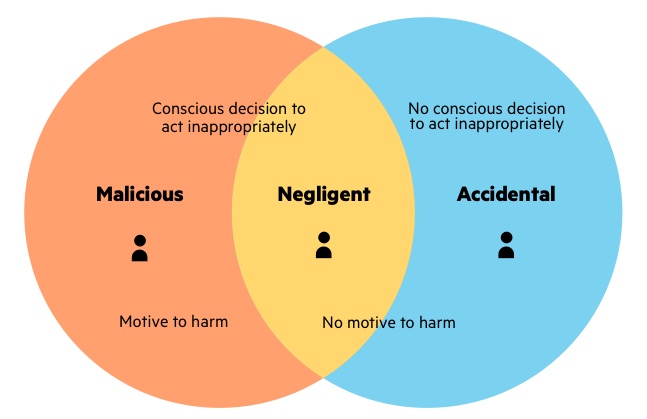 What are Cyber Security Threats? Meaning, Types and Sources – #17
What are Cyber Security Threats? Meaning, Types and Sources – #17
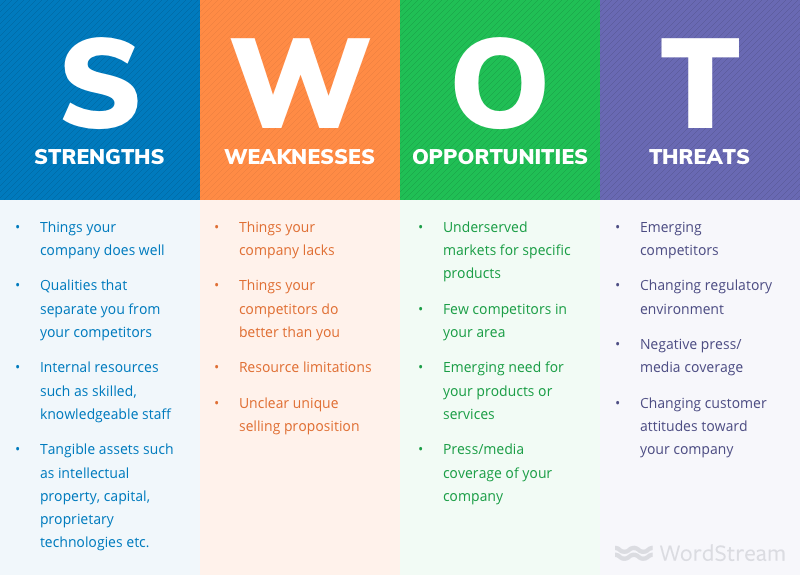
 pestleanalysis.com/wp-content/uploads/2016/06/swot… – #18
pestleanalysis.com/wp-content/uploads/2016/06/swot… – #18
 cdn.ttgtmedia.com/rms/onlineimages/security-inside… – #19
cdn.ttgtmedia.com/rms/onlineimages/security-inside… – #19
 Talent-Unleashed – #20
Talent-Unleashed – #20
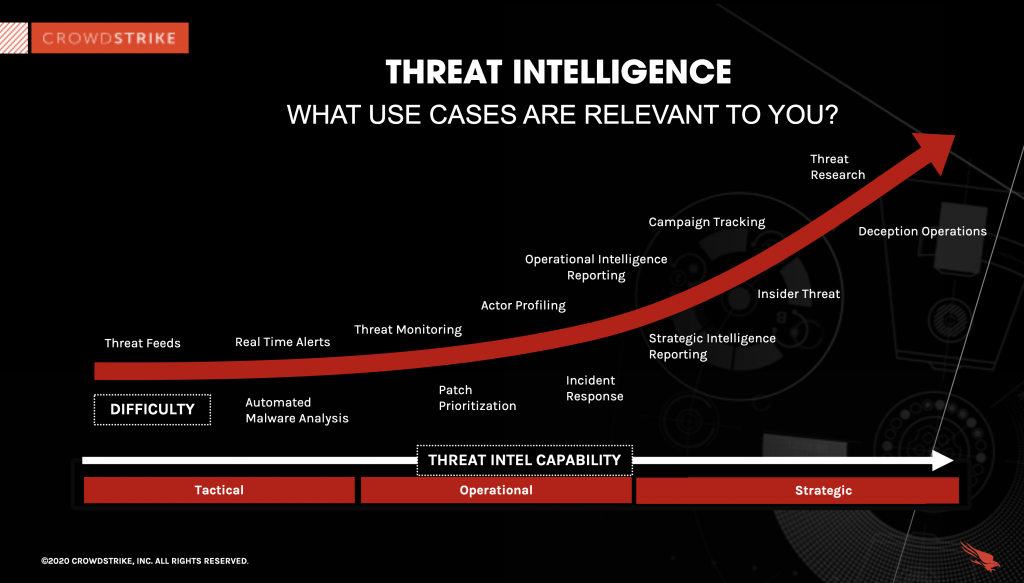
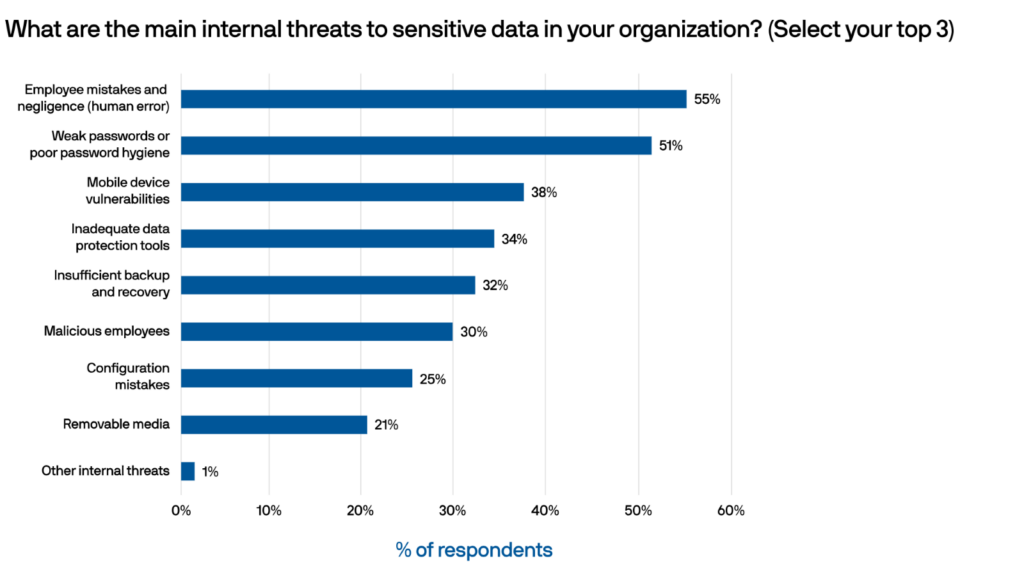 www.crowdstrike.com/wp-content/uploads/2019/07/thr… – #21
www.crowdstrike.com/wp-content/uploads/2019/07/thr… – #21
 cdn.vox-cdn.com/thumbor/3O1YdlLmifvvbu2Un08WLMwgQT… – #22
cdn.vox-cdn.com/thumbor/3O1YdlLmifvvbu2Un08WLMwgQT… – #22
 deltalogix.blog/wp-content/uploads/2021/07/Cyber-A… – #23
deltalogix.blog/wp-content/uploads/2021/07/Cyber-A… – #23
 RSVP on X: “Can’t wait to fully read the Power Threat Meaning Framework-alternative to medical model. Looks at how we make sense of difficult experiences & how messages from society increase feelings – #24
RSVP on X: “Can’t wait to fully read the Power Threat Meaning Framework-alternative to medical model. Looks at how we make sense of difficult experiences & how messages from society increase feelings – #24
 Obt threat pose : r/tarantulas – #25
Obt threat pose : r/tarantulas – #25
 helpfulprofessor.com/wp-content/uploads/2023/05/pr… – #26
helpfulprofessor.com/wp-content/uploads/2023/05/pr… – #26
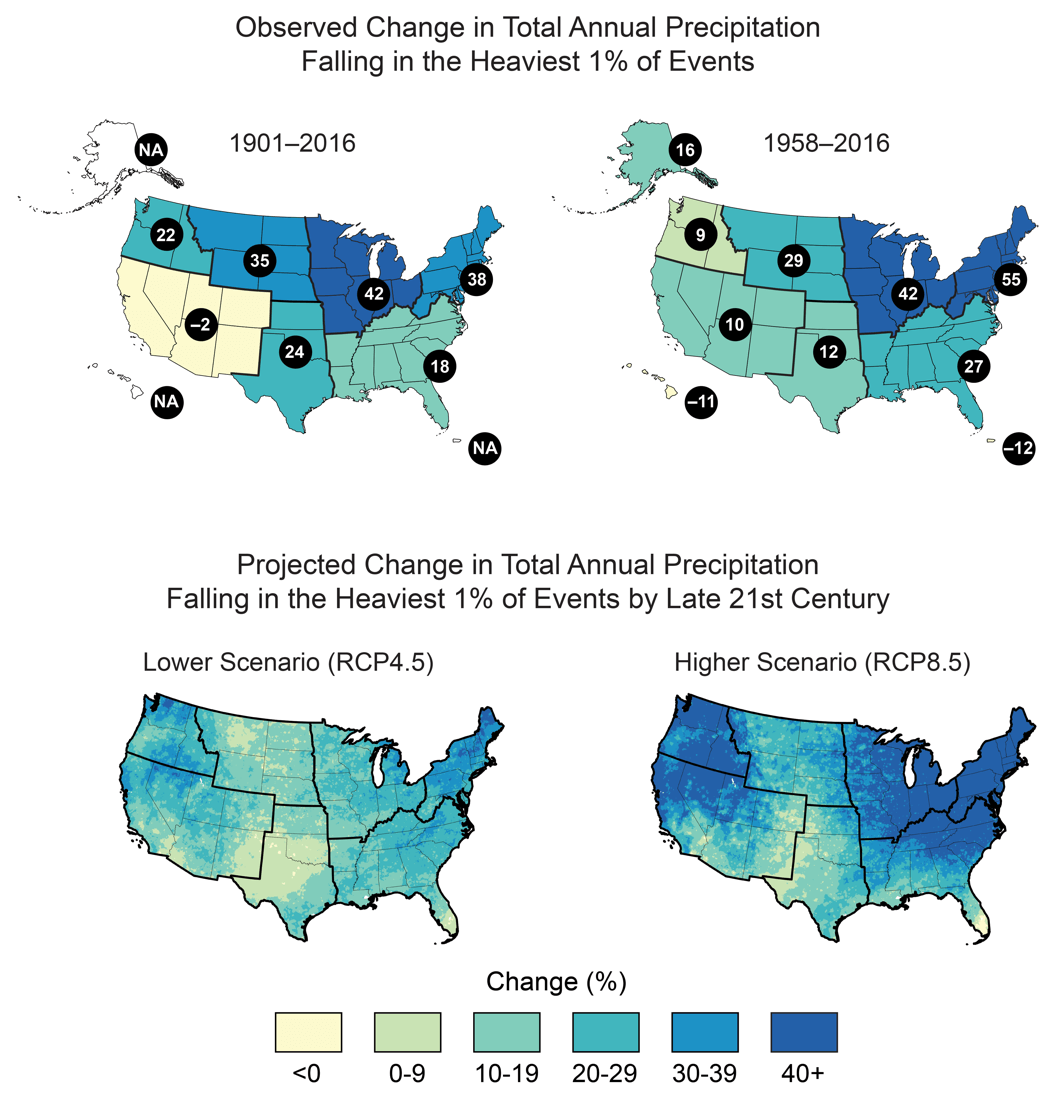 img.youtube.com/vi/5-w7wHntKGM/hqdefault.jpg – #27
img.youtube.com/vi/5-w7wHntKGM/hqdefault.jpg – #27
 Peachjar Flyers – #28
Peachjar Flyers – #28
 What is the Cyber Threat Landscape? | UpGuard – #29
What is the Cyber Threat Landscape? | UpGuard – #29
 www.dictionary.com/e/wp-content/uploads/2019/12/ex… – #30
www.dictionary.com/e/wp-content/uploads/2019/12/ex… – #30
 The British Journal of General Practice on X: “Mental health in context: structural vulnerability and support in primary care https://t.co/qLqGiZDjdd https://t.co/WoTrBccm88” / X – #31
The British Journal of General Practice on X: “Mental health in context: structural vulnerability and support in primary care https://t.co/qLqGiZDjdd https://t.co/WoTrBccm88” / X – #31
 thecyphere.com/wp-content/uploads/2021/11/insider-… – #32
thecyphere.com/wp-content/uploads/2021/11/insider-… – #32
 www.servicenow.com/content/dam/servicenow-assets/p… – #33
www.servicenow.com/content/dam/servicenow-assets/p… – #33
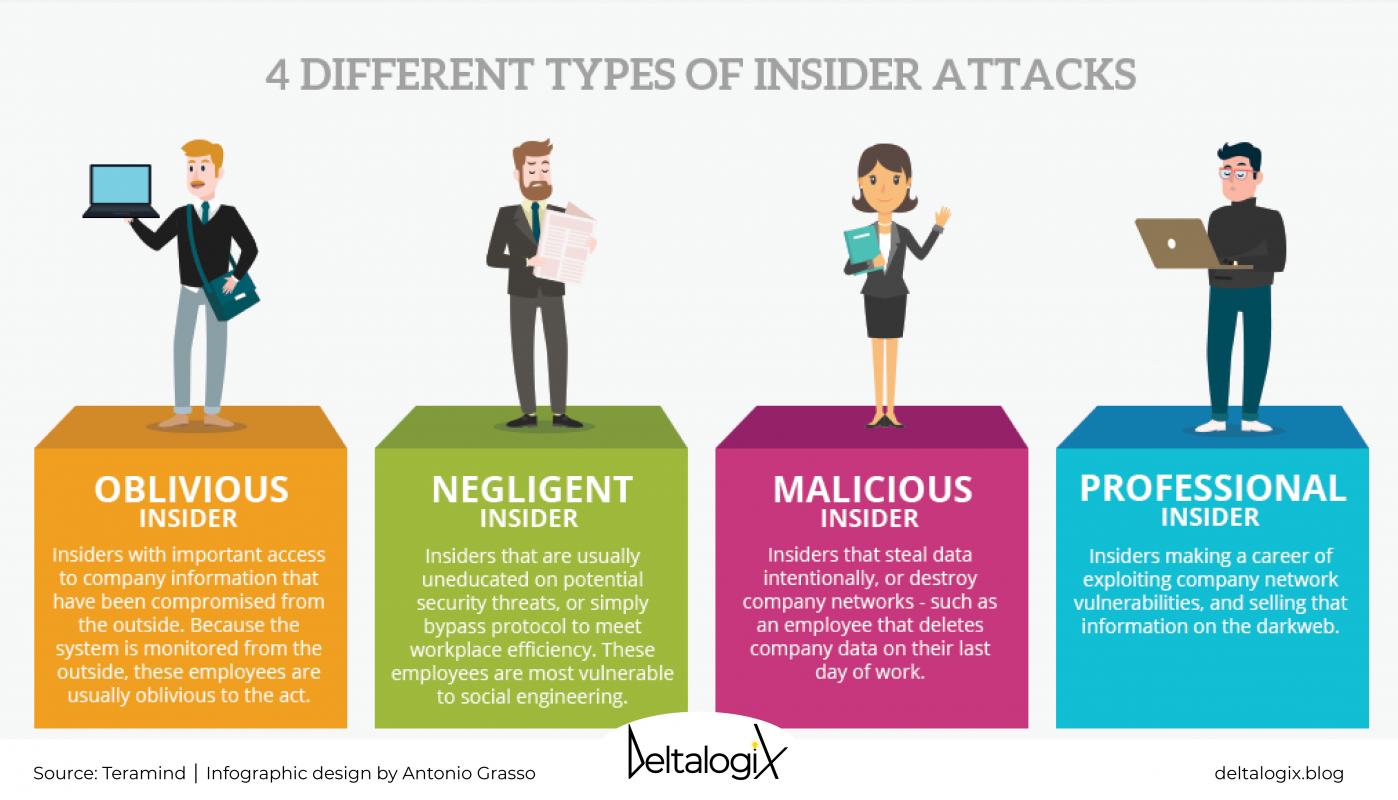 Threat Detection and Threat Prevention: Tools and Tech – #34
Threat Detection and Threat Prevention: Tools and Tech – #34
 Threat – Definition, Meaning & Synonyms | Vocabulary.com – #35
Threat – Definition, Meaning & Synonyms | Vocabulary.com – #35
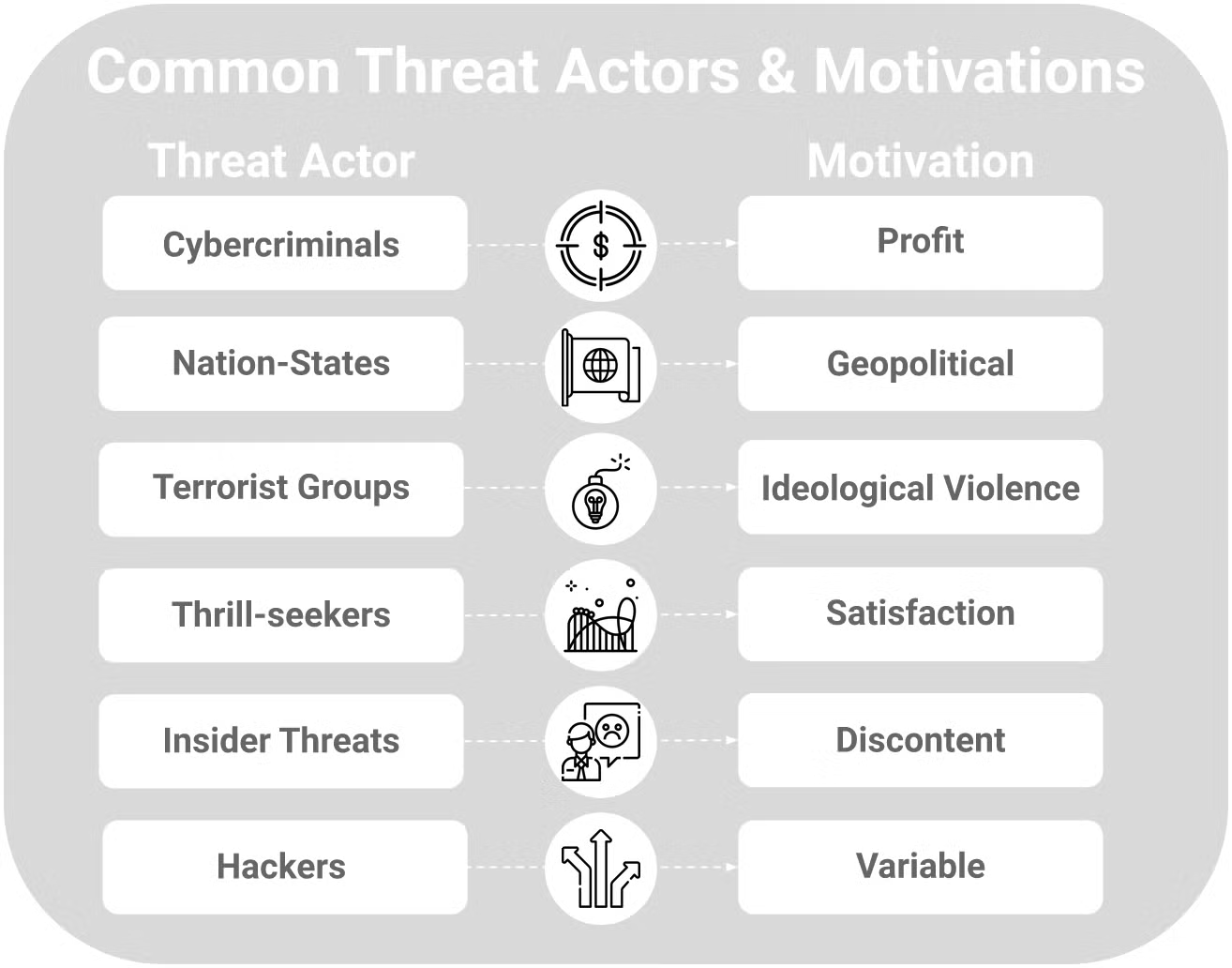
 What is a Threat Actor? – Types & Examples – #36
What is a Threat Actor? – Types & Examples – #36
 The Danger of Prison Radicalization in the West – Combating Terrorism Center at West Point – #37
The Danger of Prison Radicalization in the West – Combating Terrorism Center at West Point – #37
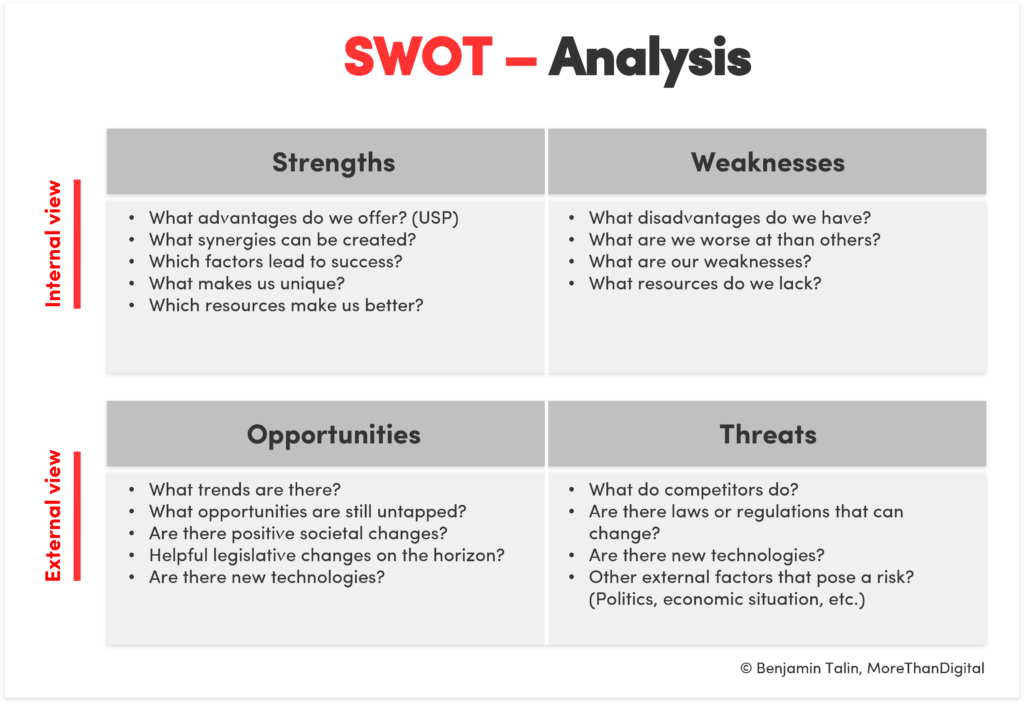 miro.medium.com/v2/resize:fit:1146/1*B4Azul5D-guVZ… – #38
miro.medium.com/v2/resize:fit:1146/1*B4Azul5D-guVZ… – #38
 Threat of New Entrants – Important Component of Industry Analysis – #39
Threat of New Entrants – Important Component of Industry Analysis – #39
 State of Insider Threats in the Digital Workplace 2019 | BetterCloud – #40
State of Insider Threats in the Digital Workplace 2019 | BetterCloud – #40
- school threat assessment
- icon threat actor
- threat actor image
 supplychaintoday.com/stage/wp-content/uploads/2018… – #41
supplychaintoday.com/stage/wp-content/uploads/2018… – #41
 www.eccouncil.org/cybersecurity-exchange/wp-conten… – #42
www.eccouncil.org/cybersecurity-exchange/wp-conten… – #42
 thecyphere.com/wp-content/uploads/2021/11/What-is-… – #43
thecyphere.com/wp-content/uploads/2021/11/What-is-… – #43
 Cluster Munitions , their threats and Convention on Cluster Munitions. #upsc#ppsc#civilservices#aeskkp#ashutosheducationalservices#career… | Instagram – #44
Cluster Munitions , their threats and Convention on Cluster Munitions. #upsc#ppsc#civilservices#aeskkp#ashutosheducationalservices#career… | Instagram – #44
 www.thesaurus.com/e/wp-content/uploads/2024/02/ecs… – #45
www.thesaurus.com/e/wp-content/uploads/2024/02/ecs… – #45
 Frontiers | A will-o’-the wisp? On the utility of voluntary contributions of data and knowledge from the fishing industry to marine science – #46
Frontiers | A will-o’-the wisp? On the utility of voluntary contributions of data and knowledge from the fishing industry to marine science – #46
%2017.15.17-min.png) www.supplychaintoday.com/wp-content/uploads/2019/1… – #47
www.supplychaintoday.com/wp-content/uploads/2019/1… – #47
 National Volcano Early Warning System – monitoring volcanoes according to their threat | U.S. Geological Survey – #48
National Volcano Early Warning System – monitoring volcanoes according to their threat | U.S. Geological Survey – #48
 www.investopedia.com/thmb/ErOpYCP-uZwFuuE78PTNOhmj… – #49
www.investopedia.com/thmb/ErOpYCP-uZwFuuE78PTNOhmj… – #49
 The Power Threat Meaning Framework: Summary | PDF | Psychological Trauma | Mental Health – #50
The Power Threat Meaning Framework: Summary | PDF | Psychological Trauma | Mental Health – #50
 Pose a threat to synonyms that belongs to phrases – #51
Pose a threat to synonyms that belongs to phrases – #51
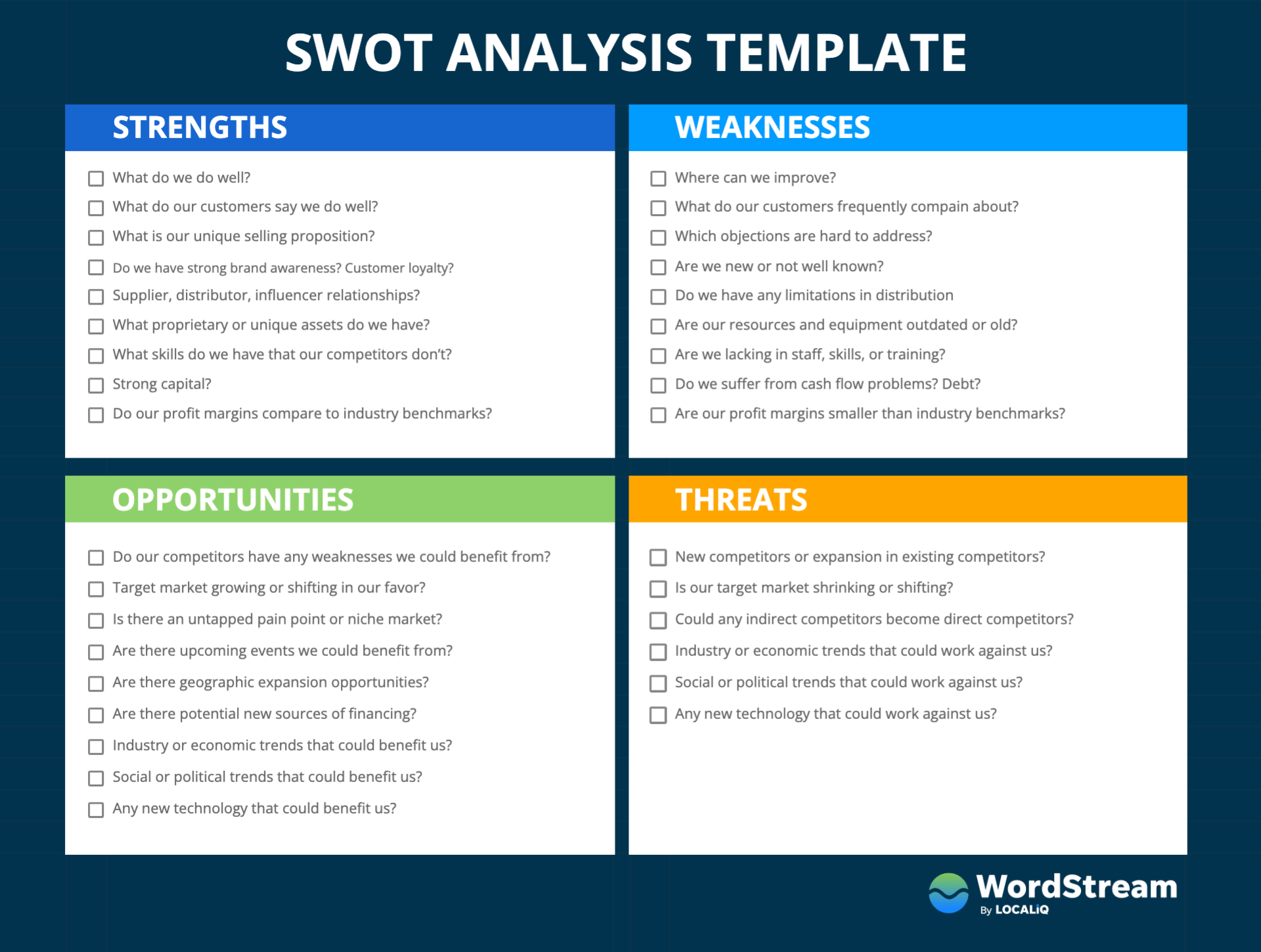
 www.wordstream.com/wp-content/uploads/2022/01/swot… – #52
www.wordstream.com/wp-content/uploads/2022/01/swot… – #52
 Porter’s Five Forces Analysis: Definition, Model & Examples Explained – #53
Porter’s Five Forces Analysis: Definition, Model & Examples Explained – #53
 23 Pose a threat to Synonyms. Similar words for Pose a threat to. – #54
23 Pose a threat to Synonyms. Similar words for Pose a threat to. – #54
 Meta’s Adversarial Threat Report, First Quarter 2023 | Meta – #55
Meta’s Adversarial Threat Report, First Quarter 2023 | Meta – #55
 PDF) What really is meant by a ‘Substantial Threat’ of Pollution? -an examination of the term’s meaning in the United States and elsewhere | Erika Lindholm – Academia.edu – #56
PDF) What really is meant by a ‘Substantial Threat’ of Pollution? -an examination of the term’s meaning in the United States and elsewhere | Erika Lindholm – Academia.edu – #56
 What Is Cyber Reconnaissance? – SentinelOne – #57
What Is Cyber Reconnaissance? – SentinelOne – #57
 What is…risk, threat, hazard, danger, harm, peril, safety, security & management thereof…according to ChatGPT (Artificial Intelligence) – #58
What is…risk, threat, hazard, danger, harm, peril, safety, security & management thereof…according to ChatGPT (Artificial Intelligence) – #58
 What is a Threat Actor? | IBM – #59
What is a Threat Actor? | IBM – #59
 Advertiser backlash may pose mortal threat to Elon Musk’s X | TPR – #60
Advertiser backlash may pose mortal threat to Elon Musk’s X | TPR – #60
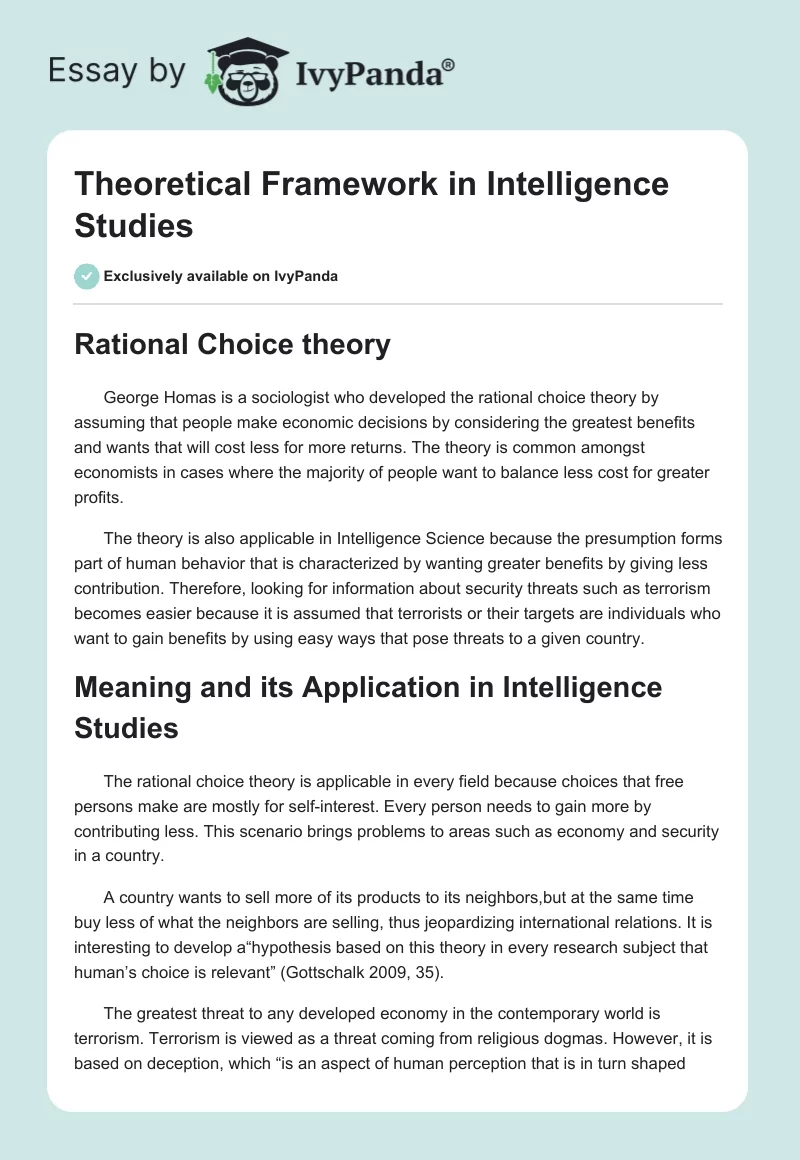
 Theoretical Framework in Intelligence Studies – 607 Words | Critical Writing Example – #61
Theoretical Framework in Intelligence Studies – 607 Words | Critical Writing Example – #61
 What is Ransomware? – #62
What is Ransomware? – #62
 POSE definition in American English | Collins English Dictionary – #63
POSE definition in American English | Collins English Dictionary – #63
 images.squarespace-cdn.com/content/v1/63ee4e042f08… – #64
images.squarespace-cdn.com/content/v1/63ee4e042f08… – #64
 Cyber Threat Intelligence: Benefits and Lifecycle | Cymune – #65
Cyber Threat Intelligence: Benefits and Lifecycle | Cymune – #65
 Google appears to be malware and poses a high risk : r/google – #66
Google appears to be malware and poses a high risk : r/google – #66
 POSE | definition in the Cambridge English Dictionary – #67
POSE | definition in the Cambridge English Dictionary – #67
 Pose A Threat synonyms – 263 Words and Phrases for Pose A Threat – #68
Pose A Threat synonyms – 263 Words and Phrases for Pose A Threat – #68
 7 Real-Life Data Breaches Caused by Insider Threats | Ekran System – #69
7 Real-Life Data Breaches Caused by Insider Threats | Ekran System – #69
 What Is an Insider Threat | Malicious Insider Attack Examples | Imperva – #70
What Is an Insider Threat | Malicious Insider Attack Examples | Imperva – #70
 The USGS volcano threat assessment — how was it determined, and what does it mean for Yellowstone | U.S. Geological Survey – #71
The USGS volcano threat assessment — how was it determined, and what does it mean for Yellowstone | U.S. Geological Survey – #71
 What is artificial intelligence? Your AI questions, answered. – Vox – #72
What is artificial intelligence? Your AI questions, answered. – Vox – #72
 February 6, 2023 – #73
February 6, 2023 – #73
 Threat Intelligence Analyst: Key Job Roles and Requirements for Success in 2022 – Spiceworks – #74
Threat Intelligence Analyst: Key Job Roles and Requirements for Success in 2022 – Spiceworks – #74
 Digital payment: 5 mobile payment security threats | Build38 – #75
Digital payment: 5 mobile payment security threats | Build38 – #75
 Computer Security & Threat Prevention for Individuals & Organizations – Lesson | Study.com – #76
Computer Security & Threat Prevention for Individuals & Organizations – Lesson | Study.com – #76
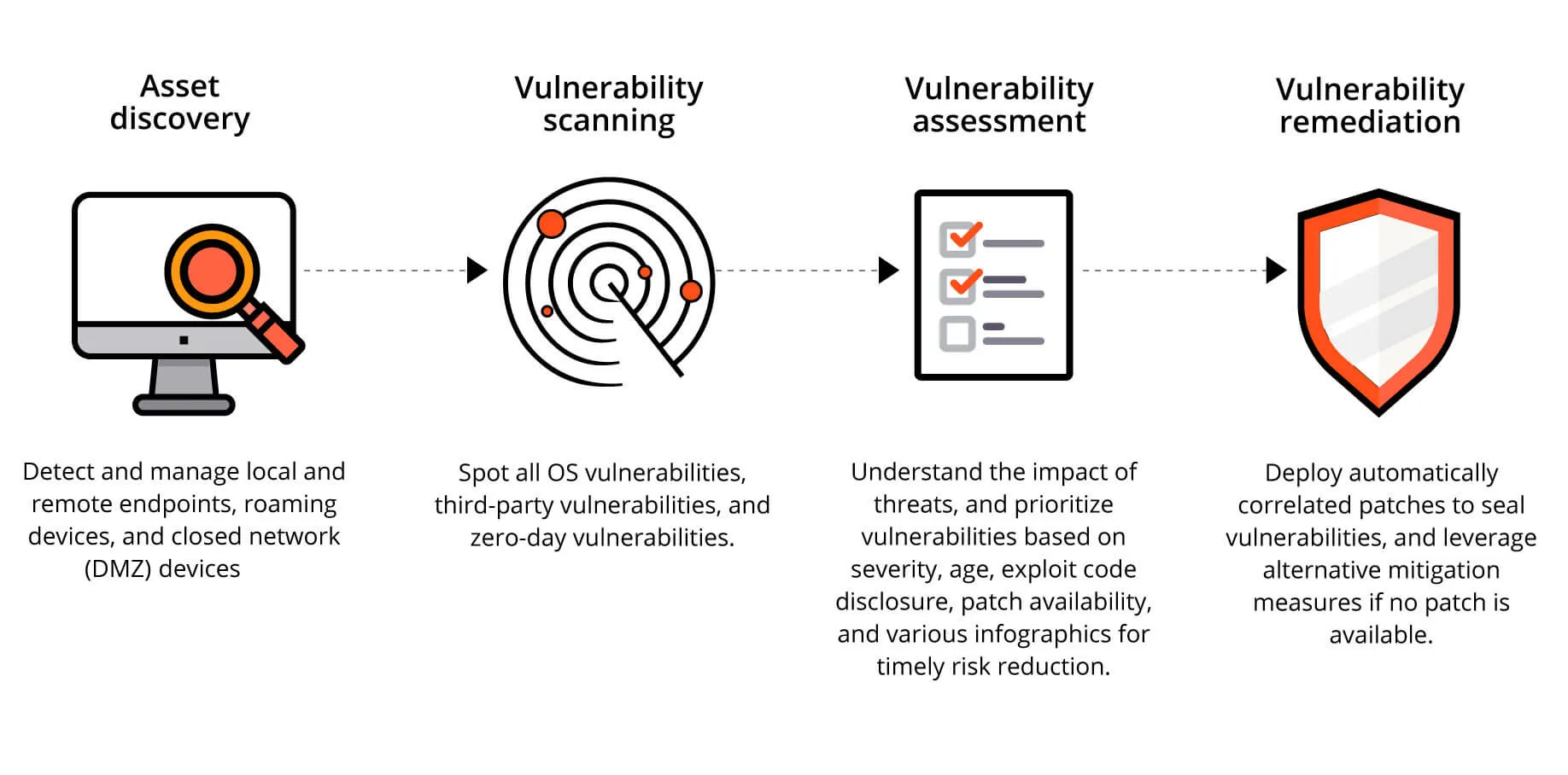
 www.eccouncil.org/wp-content/uploads/2023/01/Asset… – #77
www.eccouncil.org/wp-content/uploads/2023/01/Asset… – #77
 – #78
– #78
 – #79
– #79
 – #80
– #80
 – #81
– #81
 – #82
– #82
 – #83
– #83
 – #84
– #84
 – #85
– #85
 – #86
– #86
 – #87
– #87
 – #88
– #88
 – #89
– #89
 – #90
– #90
 – #91
– #91
 – #92
– #92
 – #93
– #93
 – #94
– #94
 – #95
– #95
 – #96
– #96
 – #97
– #97
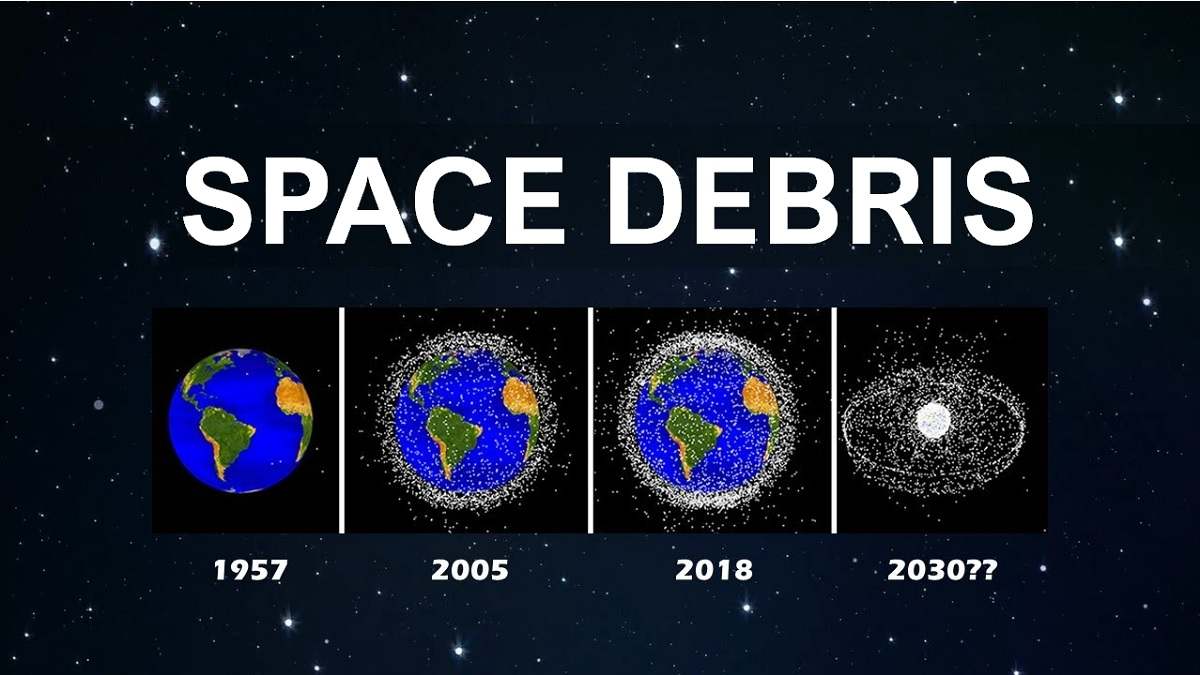
 – #98
– #98
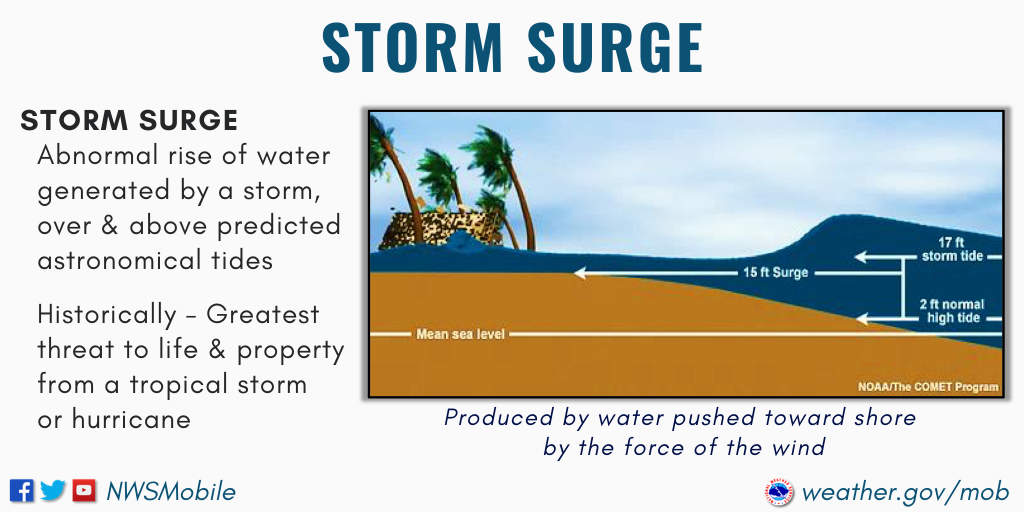 – #99
– #99
 – #100
– #100
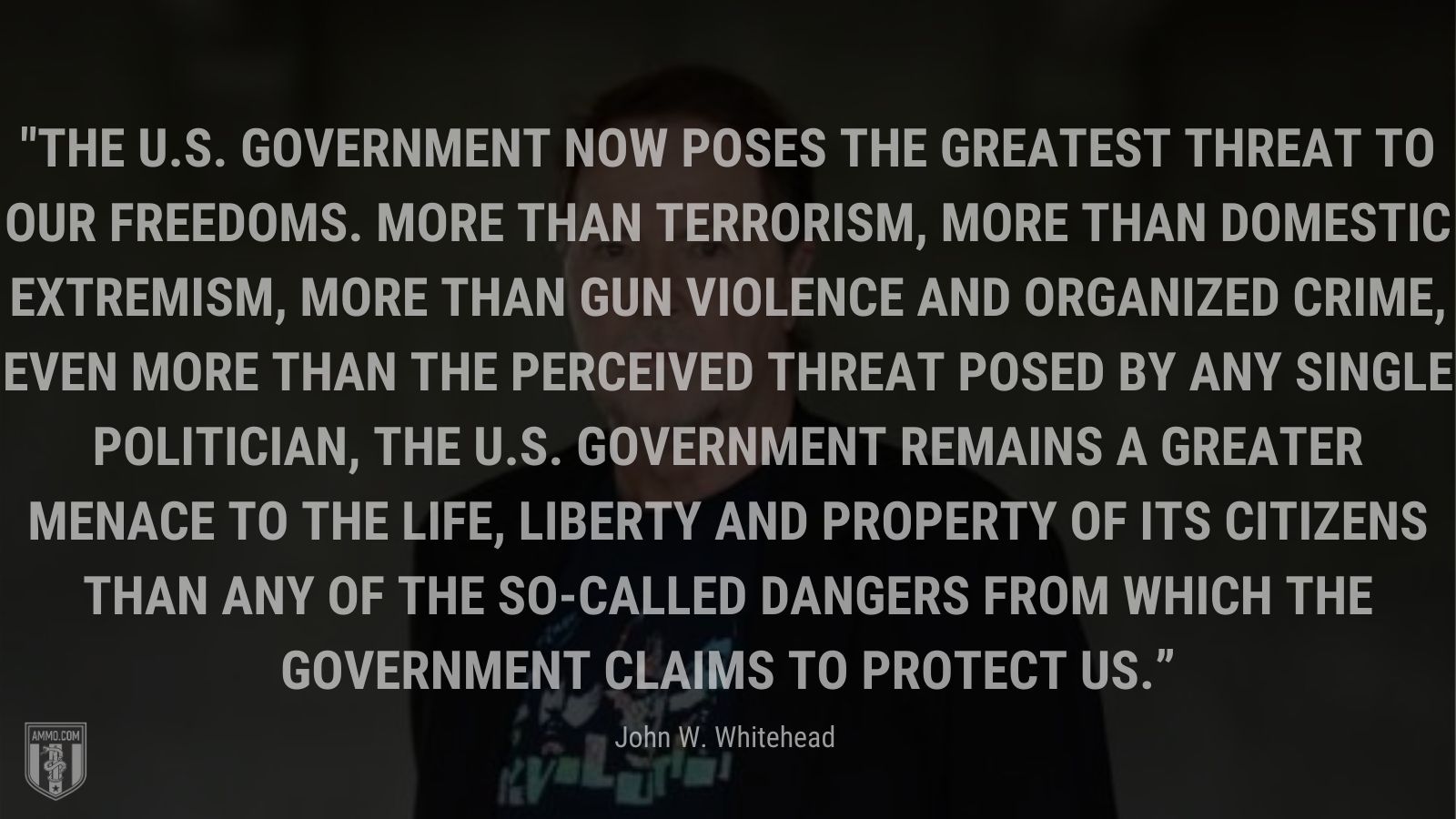 – #101
– #101
 – #102
– #102
 – #103
– #103
 – #104
– #104
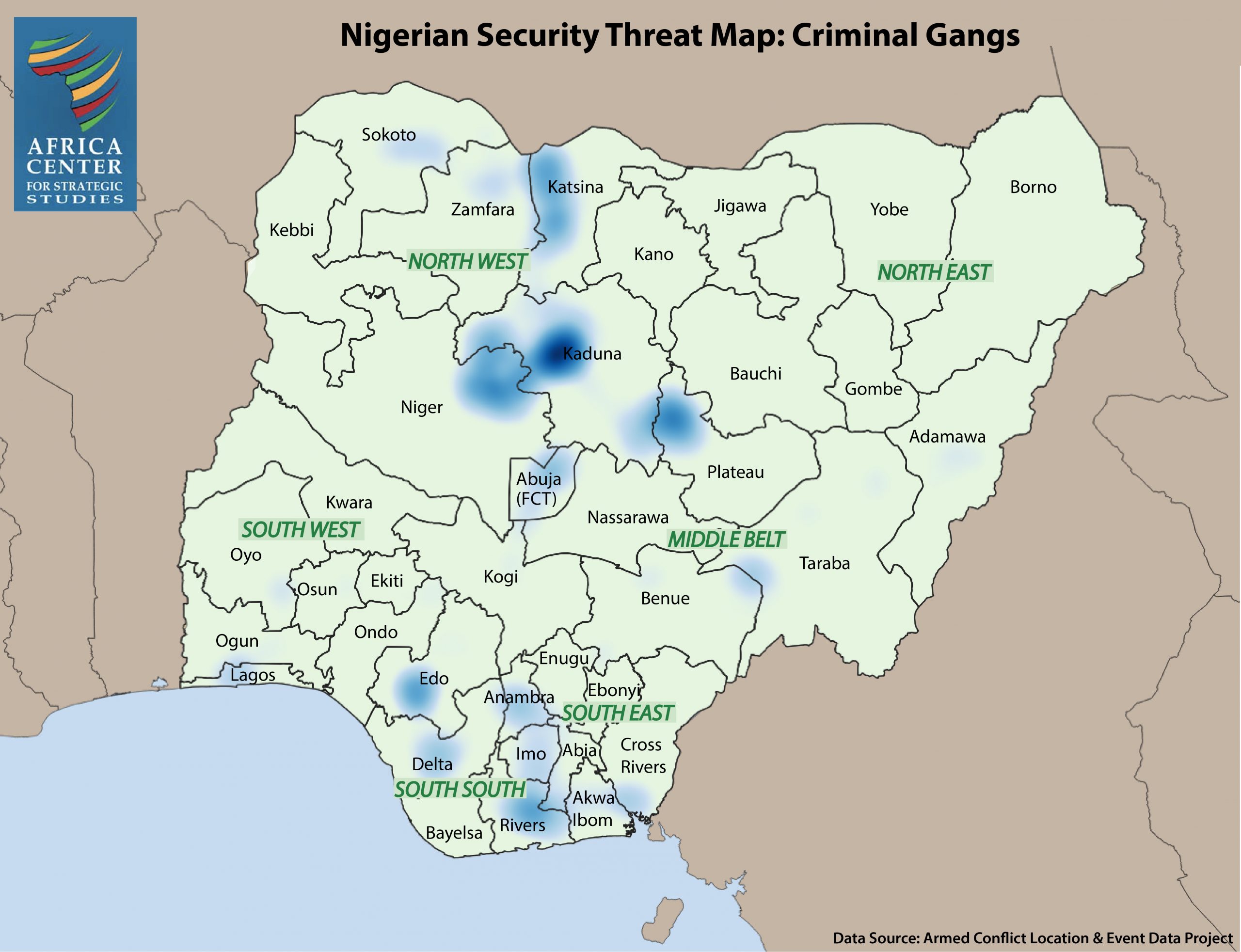 – #105
– #105
 – #106
– #106
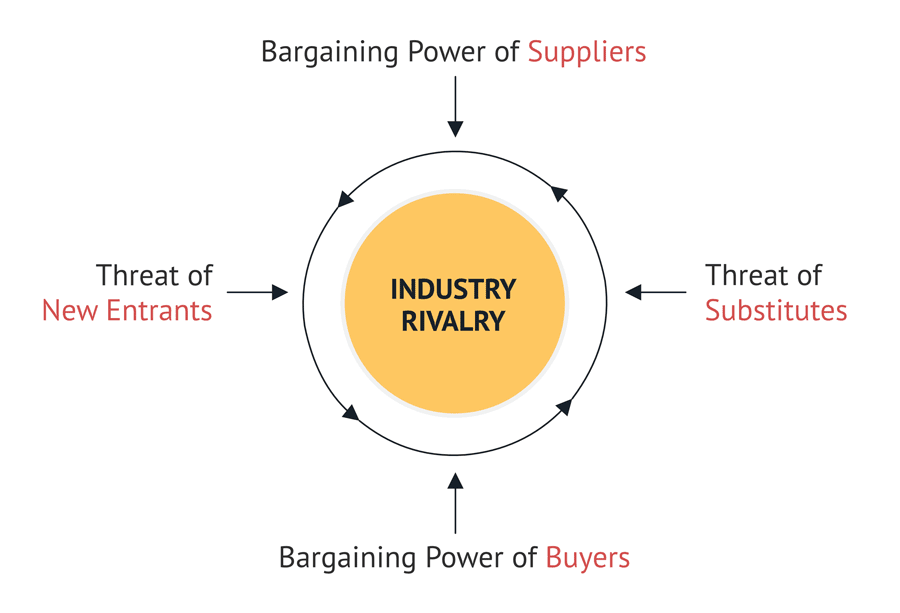 – #107
– #107
 – #108
– #108
 – #109
– #109
 – #110
– #110
- pose meaning
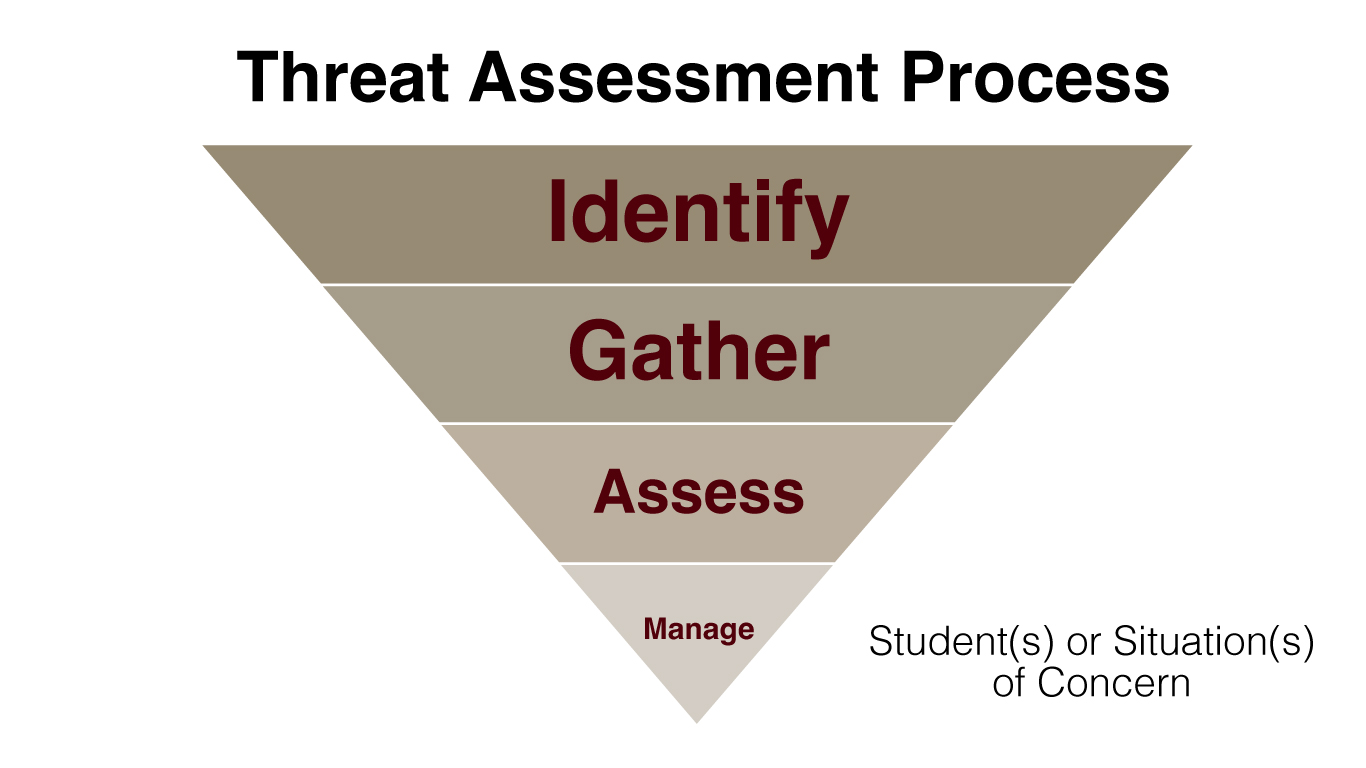
- student threat assessment template
 – #111
– #111
 – #112
– #112
 – #113
– #113
 – #114
– #114
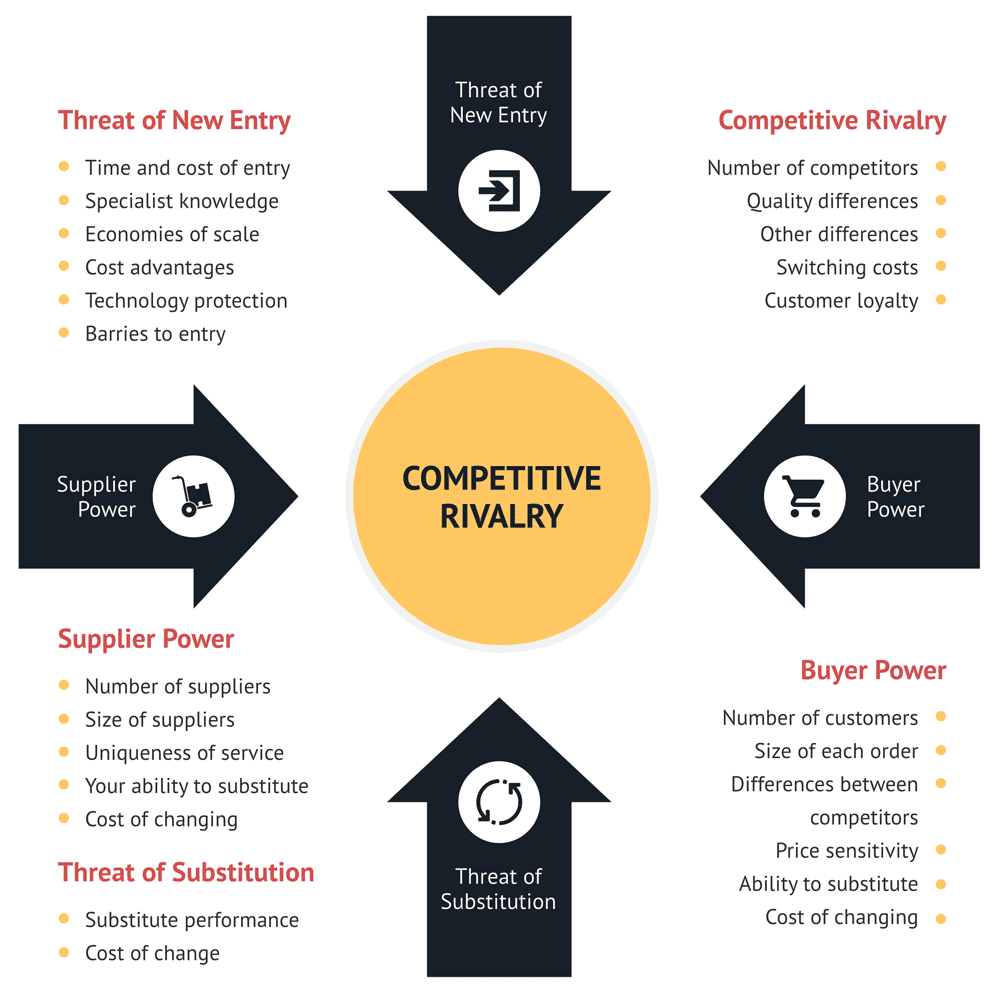 – #115
– #115
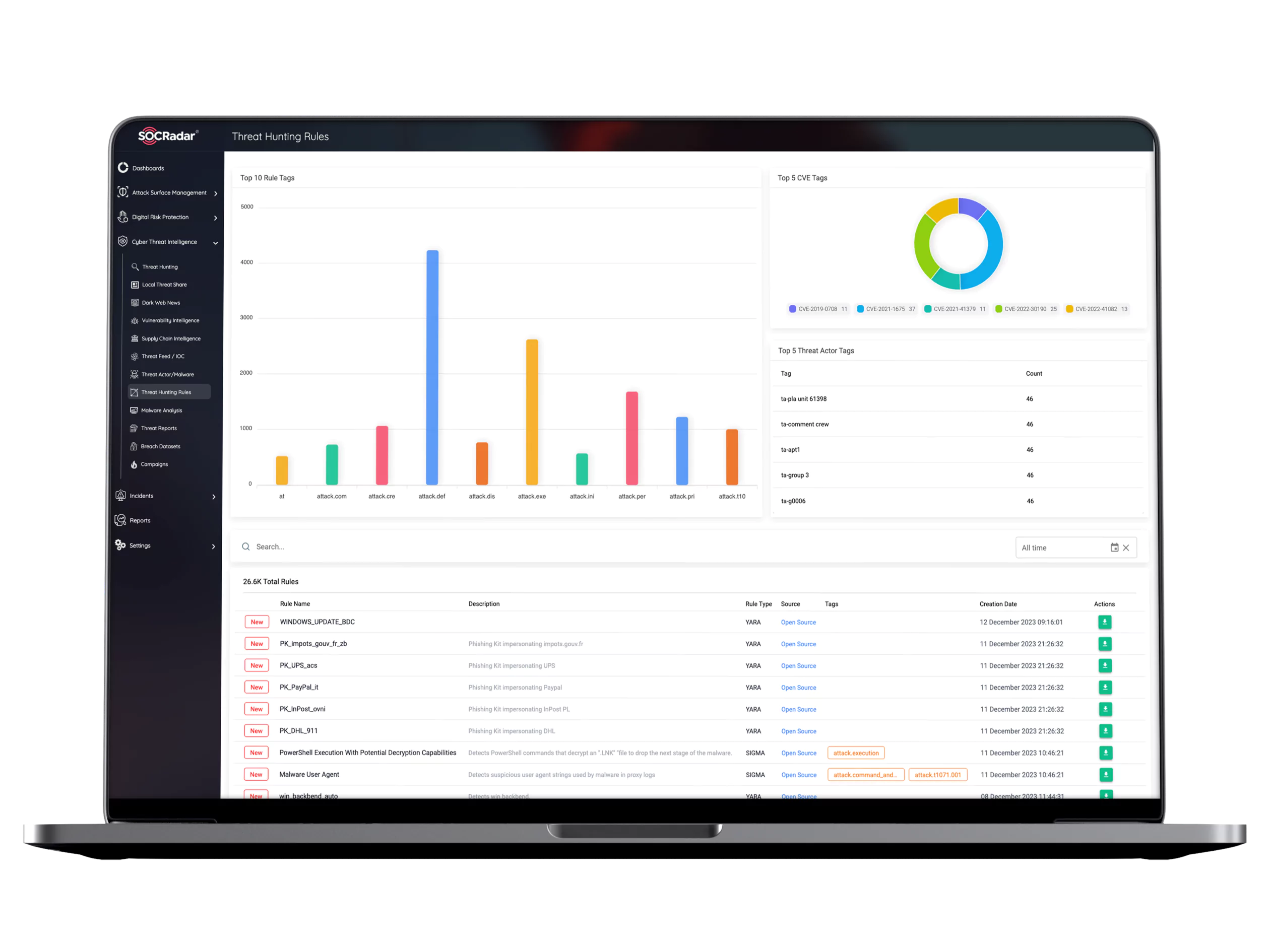 – #116
– #116
 – #117
– #117
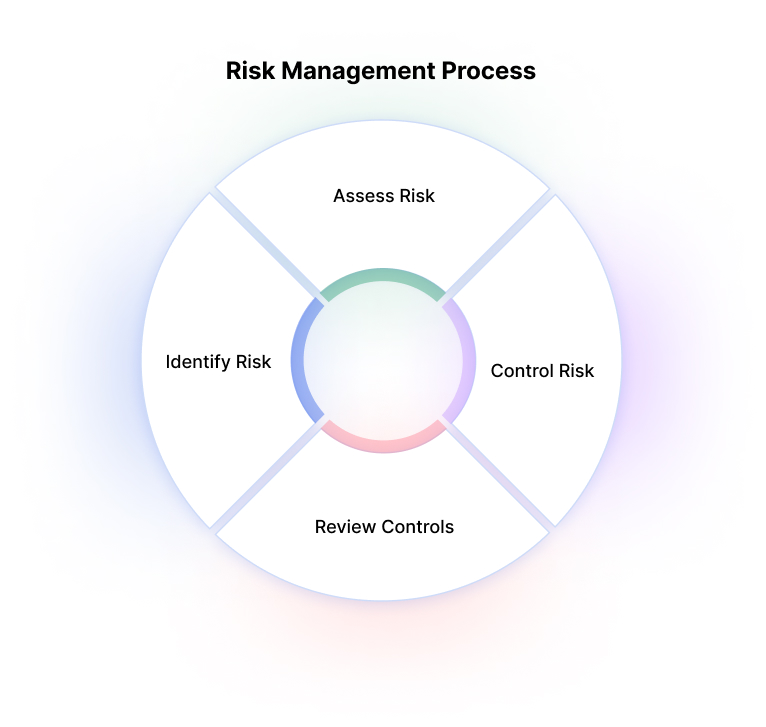 – #118
– #118
 – #119
– #119
 – #120
– #120
 – #121
– #121
 – #122
– #122
 – #123
– #123
 – #124
– #124
 – #125
– #125
 – #126
– #126
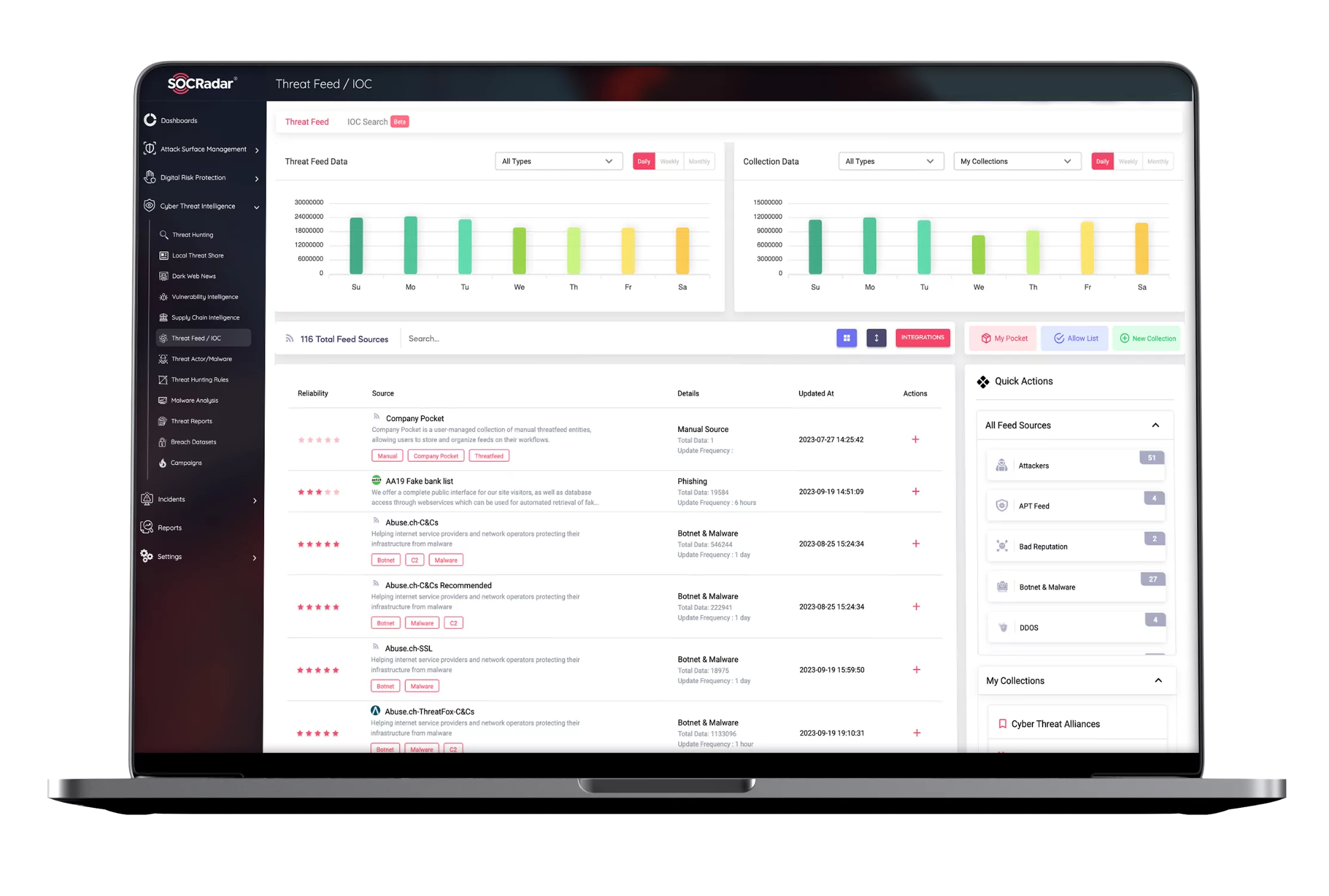 – #127
– #127
 – #128
– #128
 – #129
– #129
 – #130
– #130
 – #131
– #131
 – #132
– #132
 – #133
– #133
 – #134
– #134
 – #135
– #135
 – #136
– #136
 – #137
– #137
 – #138
– #138
 – #139
– #139
 – #140
– #140
 – #141
– #141
 – #142
– #142
 – #143
– #143
 – #144
– #144
 – #145
– #145
 – #146
– #146
 – #147
– #147
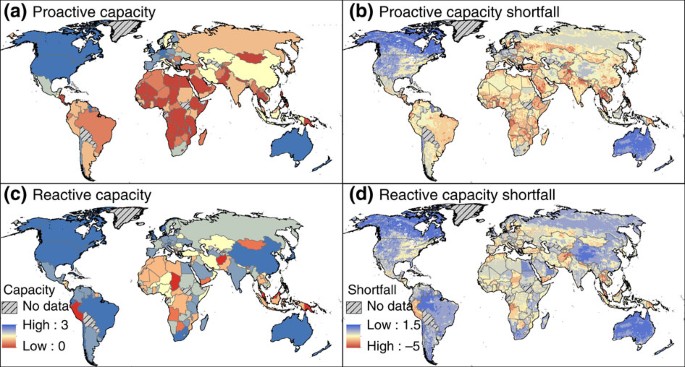 – #148
– #148
 – #149
– #149
 – #150
– #150
 – #151
– #151
 – #152
– #152
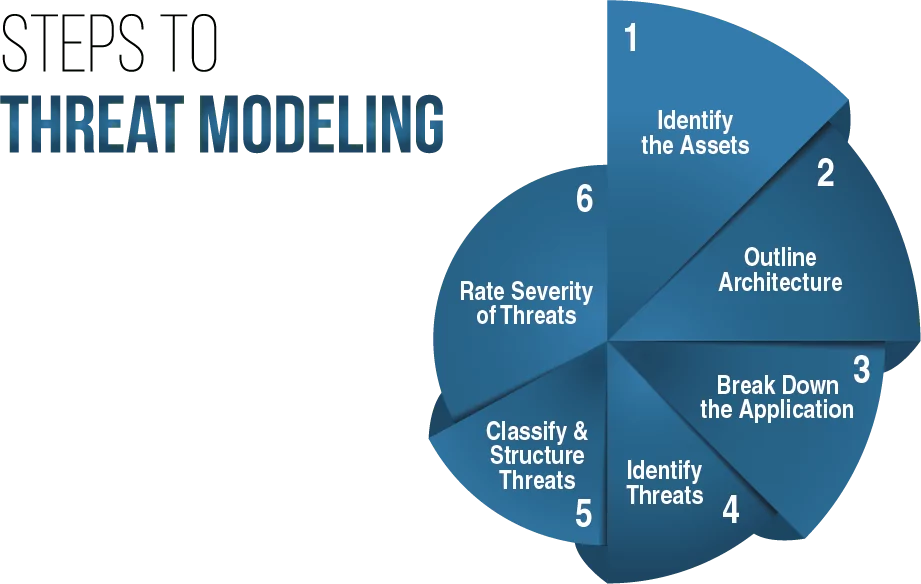 – #153
– #153
 – #154
– #154
 – #155
– #155
 – #156
– #156
 – #157
– #157
 – #158
– #158
Posts: threat posed meaning
Categories: Poses
Author: nanoginkgobiloba.vn
